
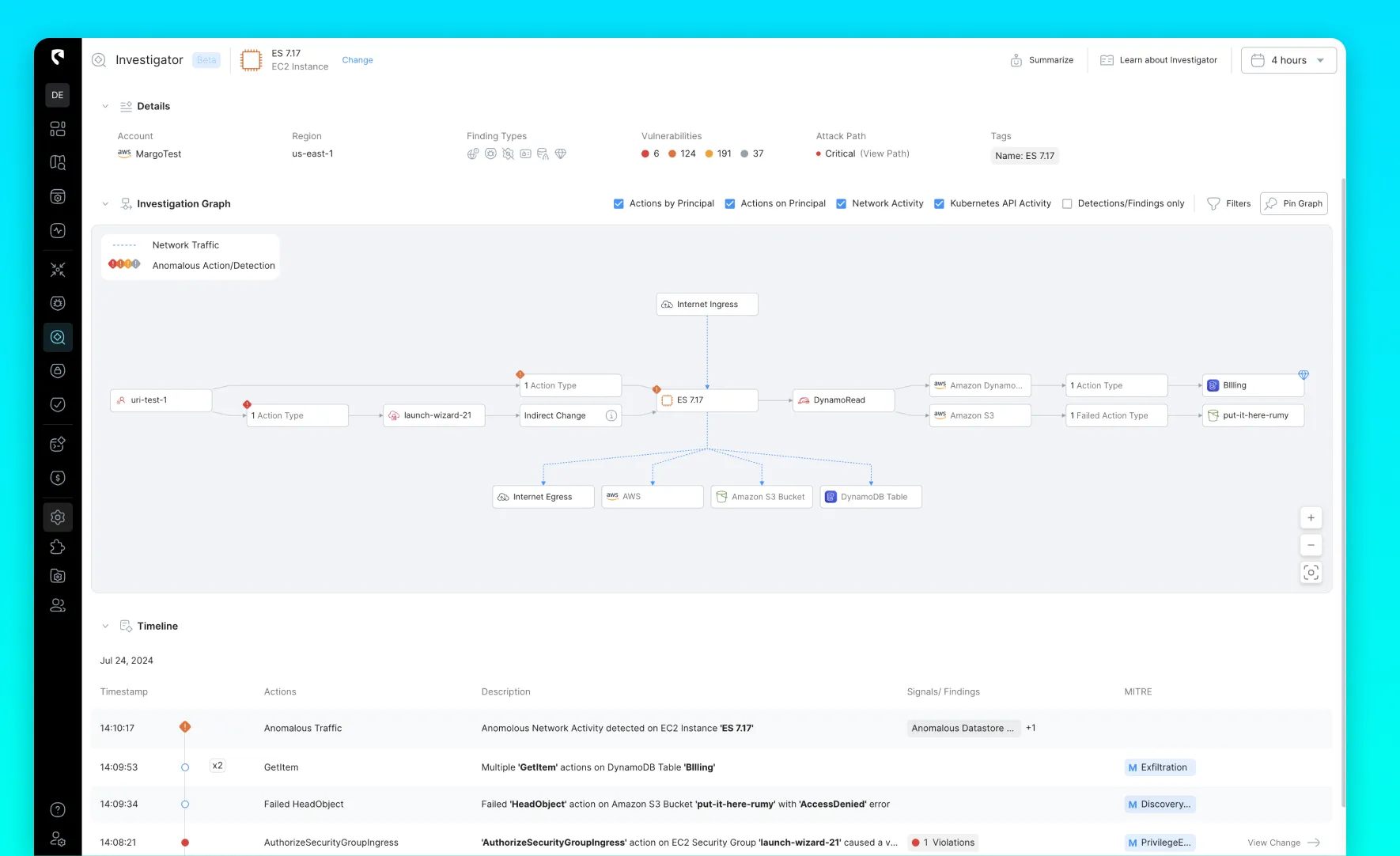
As cyber attackers become more sophisticated, leveraging a multitude of techniques to breach security defenses, organizations must have visibility into the entire attack storyline. This need has driven the strategic integration between Stream Security and CrowdStrike, combining their strengths to offer detection and response capabilities from the cloud layer down to the workload level.
Stream Security's CloudTwin® continuously monitors cloud activities and configurations in real-time. The platform uncovers adversary intent by modeling all cloud interactions, revealing detailed attack storylines and exploitability according to the unique environment properties. This approach allows organizations to detect and respond to threats with the necessary context, eliminating blind spots during attacks and providing a live cloud-state view of the environment.
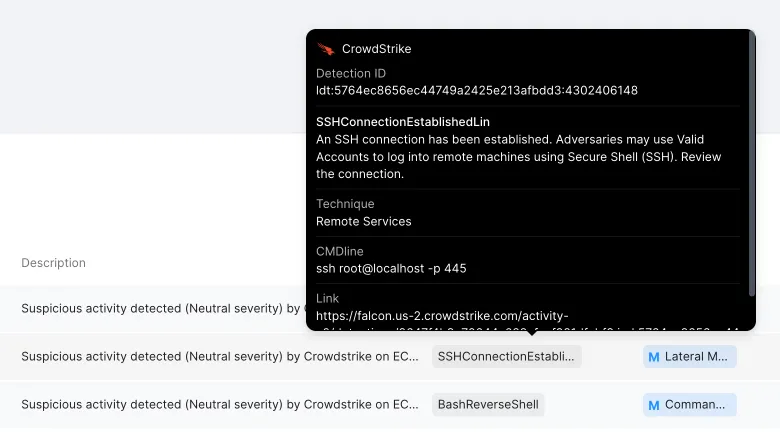
On the other hand, CrowdStrike excels in preventing threats in real-time with its industry-leading set of endpoint and workload telemetry, threat intelligence, and AI-powered analytics. CrowdStrike's Spotlight vulnerability management solution further enhances security by helping teams detect and manage susceptible assets in the cloud, ensuring that security teams are aware of their exposure.
The integration between Stream Security and CrowdStrike brings a unique approach to detecting and responding to cloud threats. Stream Security uncovers activities at the cloud layer, including behavior patterns and identity correlations, while CrowdStrike detects threats at the workload level, revealing what attackers are doing inside instances. This integration provides security teams with the ability to:
The integration between Stream Security and CrowdStrike offers a solution that seals every cloud attack all the way from accurate detection to effective response. By integrating cloud-level anomaly detection with workload-level threat detection and vulnerability management, this collaboration provides security teams with the tools they need to unveil the adversary's intent, reveal the attack’s exploitability, and predict their next move. With complete visibility, prioritized threat response, and proactive attack path analysis, organizations can outpace the adversary.
Stream.Security delivers the only cloud detection and response solution that SecOps teams can trust. Born in the cloud, Stream’s Cloud Twin solution enables real-time cloud threat and exposure modeling to accelerate response in today’s highly dynamic cloud enterprise environments. By using the Stream Security platform, SecOps teams gain unparalleled visibility and can pinpoint exposures and threats by understanding the past, present, and future of their cloud infrastructure. The AI-assisted platform helps to determine attack paths and blast radius across all elements of the cloud infrastructure to eliminate gaps accelerate MTTR by streamlining investigations, reducing knowledge gaps while maximizing team productivity and limiting burnout.