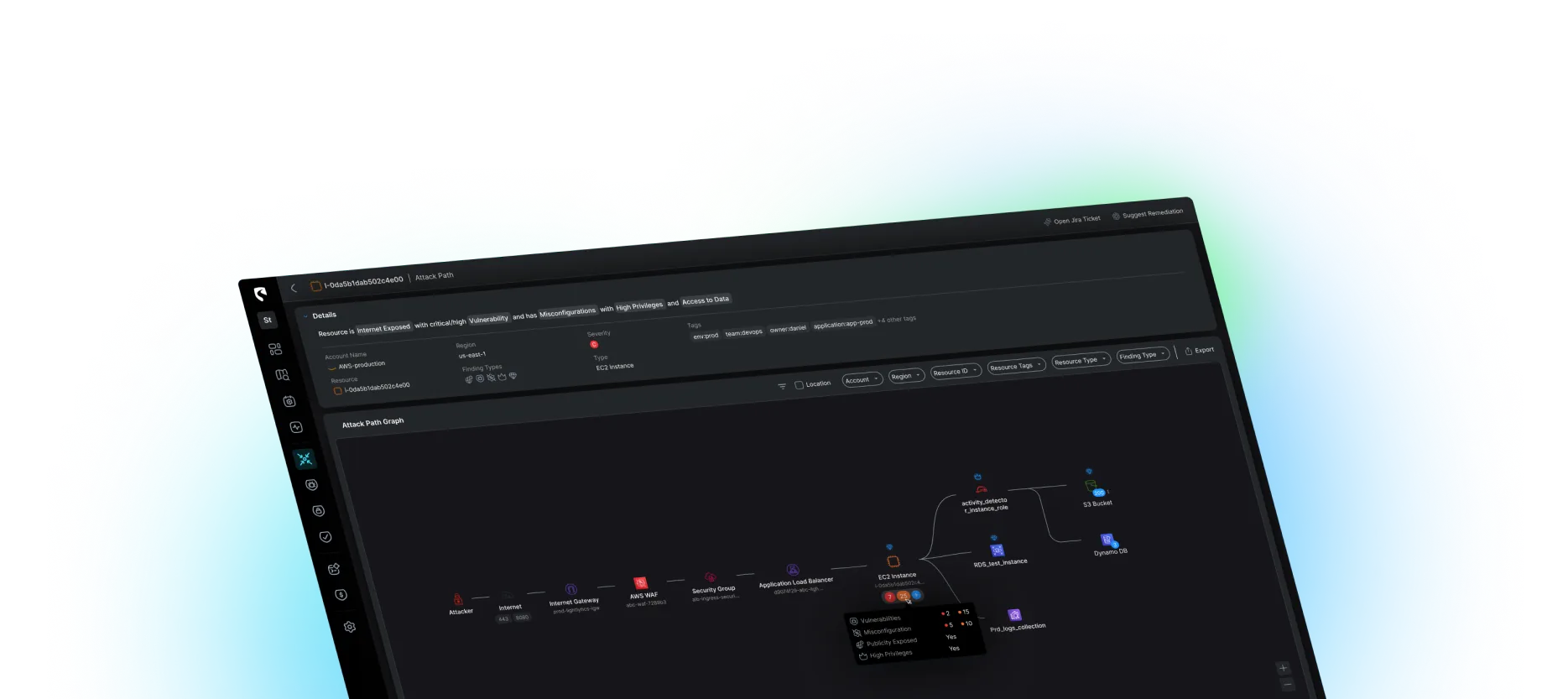
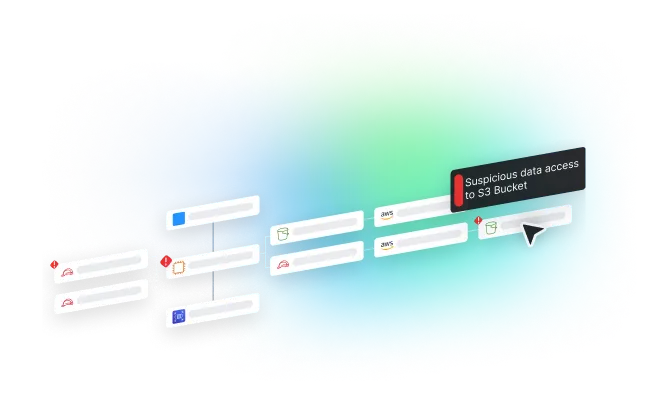
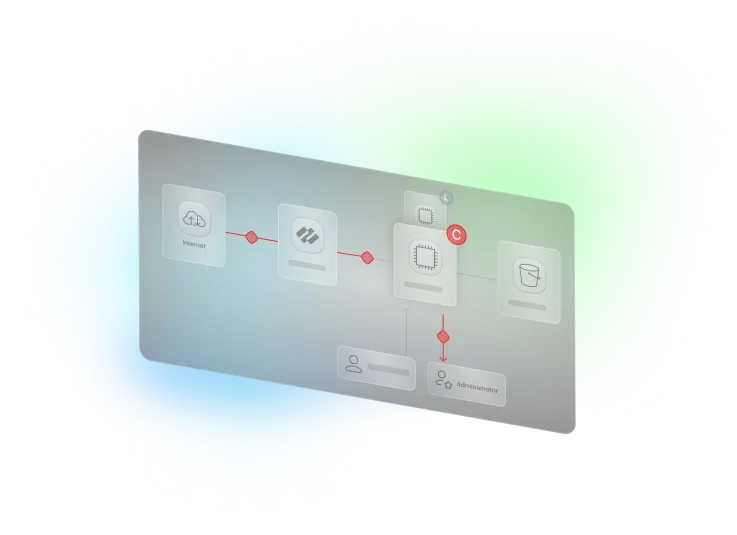
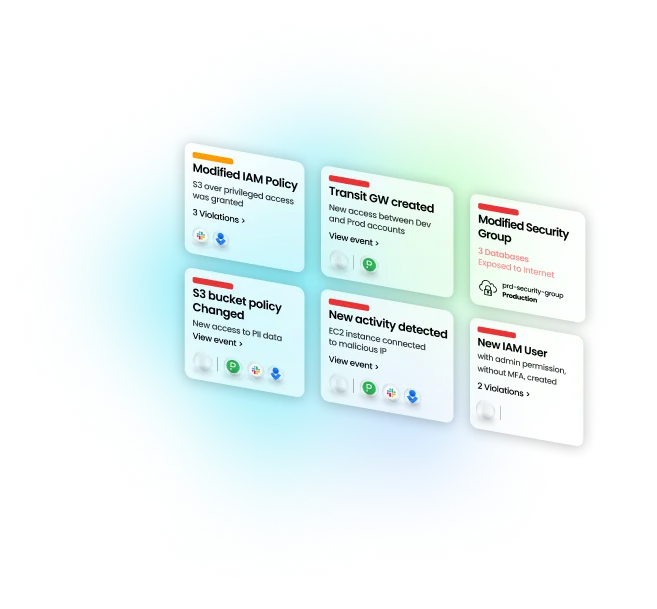
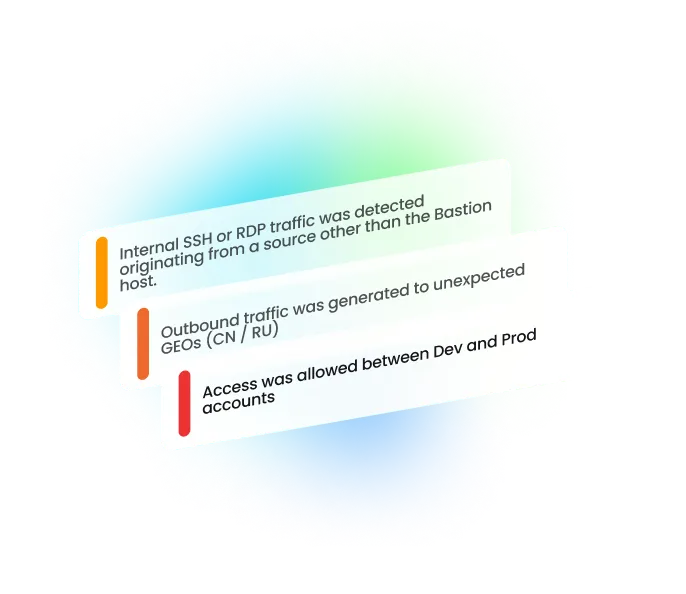
Enhance detection capabilities by defining custom policies tailored to your own threat modeling
Configure detection rules that are tailored to your cloud environment based on asset value, attack paths, connectivity, and more in an intuitive, no-code interface. Minimize time spent on false positives with seamless rule integration.