Running complex computing systems requires technology to make it easier for developers and managers to operate and constantly improve their applications. Containers are extremely effective for enterprises as well as startups Gartner predicts that 70% of global organizations will be running more than two containerized applications by 2023. Using containers reduces deployment time, review cycles and upgrades security with the inherent isolation of the product.
What is called container technology today was developed in 1979 with Unix version 7 and the chroot system. The idea was to isolate processes by restricting application access. This advance was the beginning of process isolation: segregating file access for each process. Chroot was added to BSD in 1982.
Container technology matured in the 2000s with the introduction of Free BSD Jails which are partitions of a computer on the same system. In 2001 Linux VServer was introduced and enabled the partitioning of resources. in 2005 OpenVZ , and jails were combined with boundary separation to create in Solaris Containers in 2004. After jails, container tech further progressed with the introduction of control groups in 2006.
Control Groups or cgroups were implemented for usage of resources like the CPU and memory. In 2008 they were used and built upon in Linux containers it worked on the Linux kernel without any patches.
In 2013 Docker was introduced building its foundation on two systems, LXC and libcontainers due to stable technology Docker reached 100 million downloads within a year.
In 2004 Google introduced the Borg system which was a large-scale internal cluster management system, which ran hundreds of thousands of jobs, from many thousands of different applications, across many clusters, each with up to tens of thousands of machines. In mid-2014 Google introduced Kubernetes as an open source version of Borg.July 21: Kubernetes v1.0 gets released. Along with the release, Google partnered with the Linux Foundation to form the Cloud Native Computing Foundation (CNCF).
In 2017 the open-source project demonstrated great strides towards becoming a more mature technology. Kubernetes supports increasingly complex classes of applications - enabling enterprise transition to both hybrid cloud and microservices. It was also the first project adopted by the CNCF and commands a growing list of third-party system integration service providers.
Today Kubernetes is considered the leading Container Orchestration technology with 5.6 million developers using Kubernetes worldwide, representing 31% of all backend developers.
By combining Kubernetes with the cloud layers and all the inter and intra dependencies between them, we obtain an extremely complex set of infrastructure, much like conducting as a developer you need to "hear" all the different instruments and understand the dependencies between them. The horn section needs to be in sync with violins, the flutes, percussion the conductor needs to hear all and understand how they work together to create a masterpiece.
With our CloudTwin you can detect all Kubernetes components instantly, understand the architecture of your containerized infrastructure in real-time, and see how cloud configuration changes affect Kubernetes workloads both at build and runtime. When you know how they are connected you can troubleshoot Kubernetes configurations, easily understand all dependencies, reduce downtimes and enforce best practices.
Here's how we do it:
The integration process is quick and simple, deploy our Helm chart and you are ready to go:
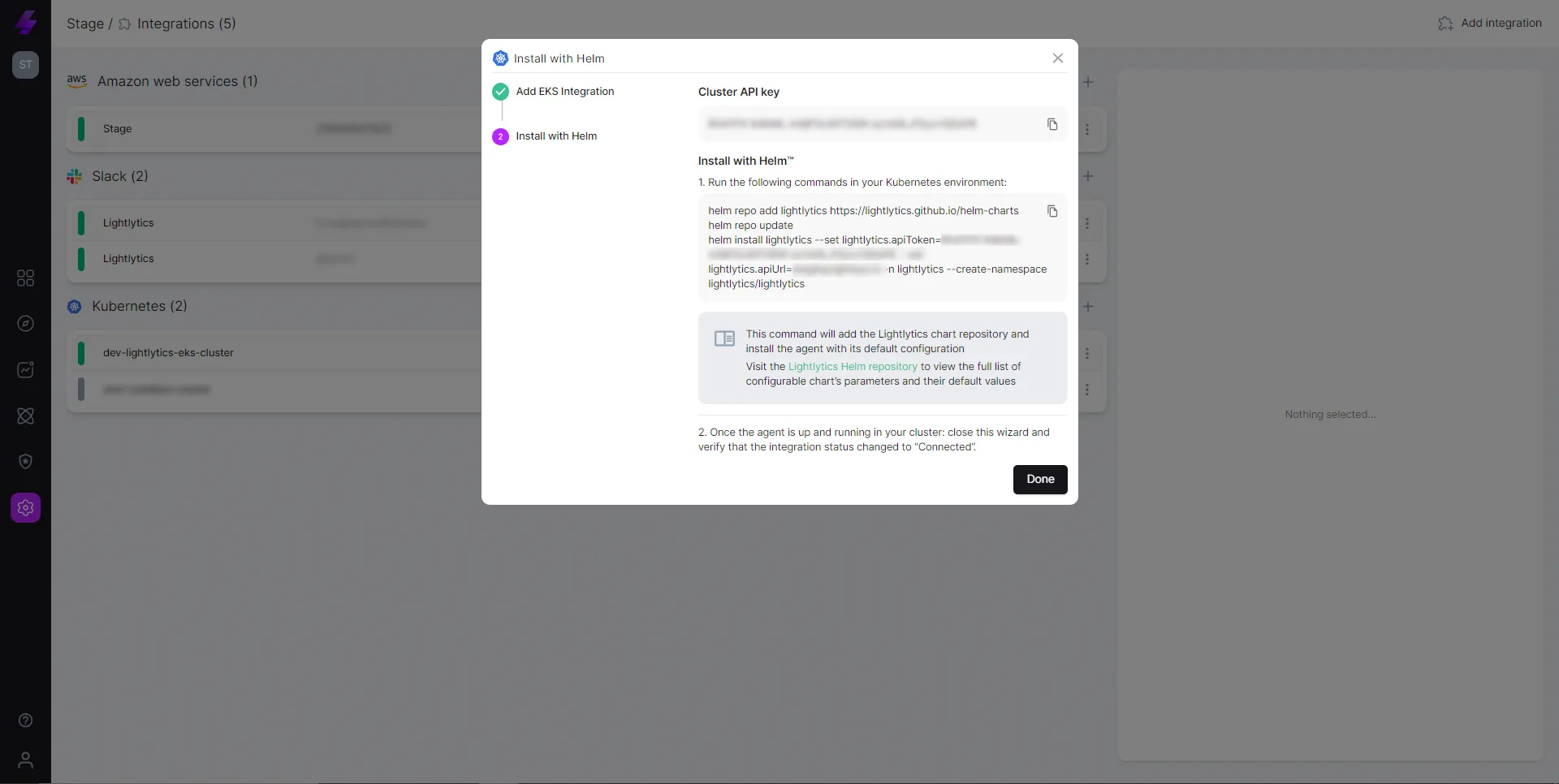
Identify all Kubernetes cluster resources and configurations, as well as their dependencies with the cloud infrastructure services across multiple accounts.
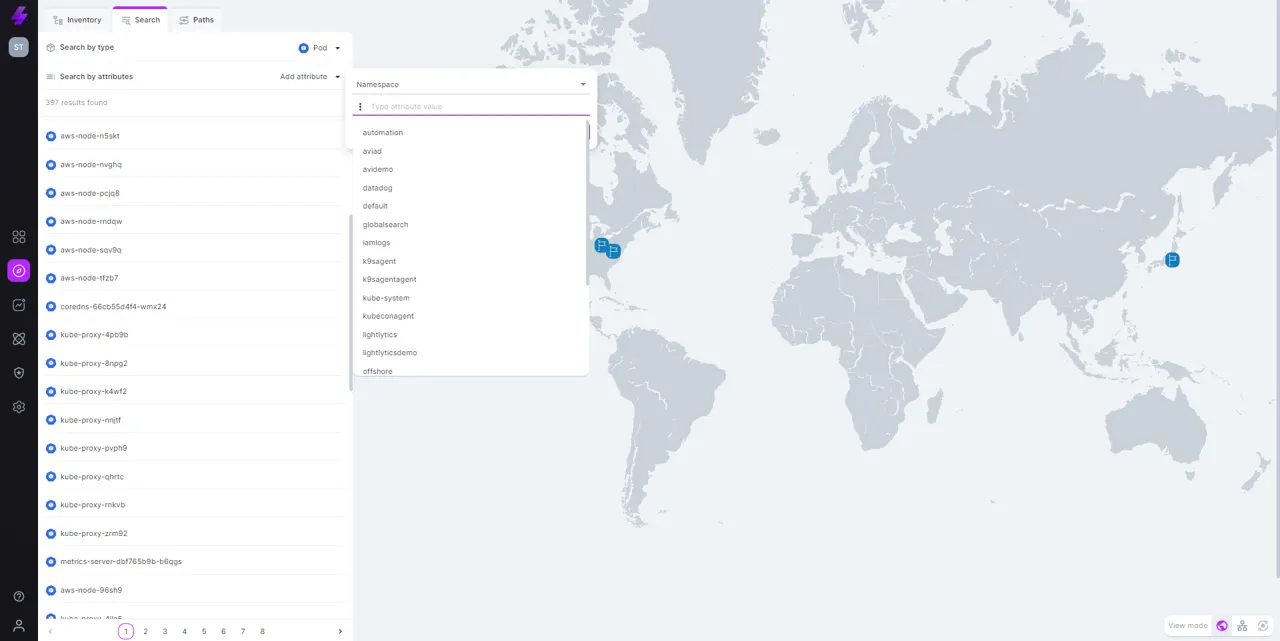
Get a full inventory of all k8s resources in your cloud environment

Get the full context of any resource
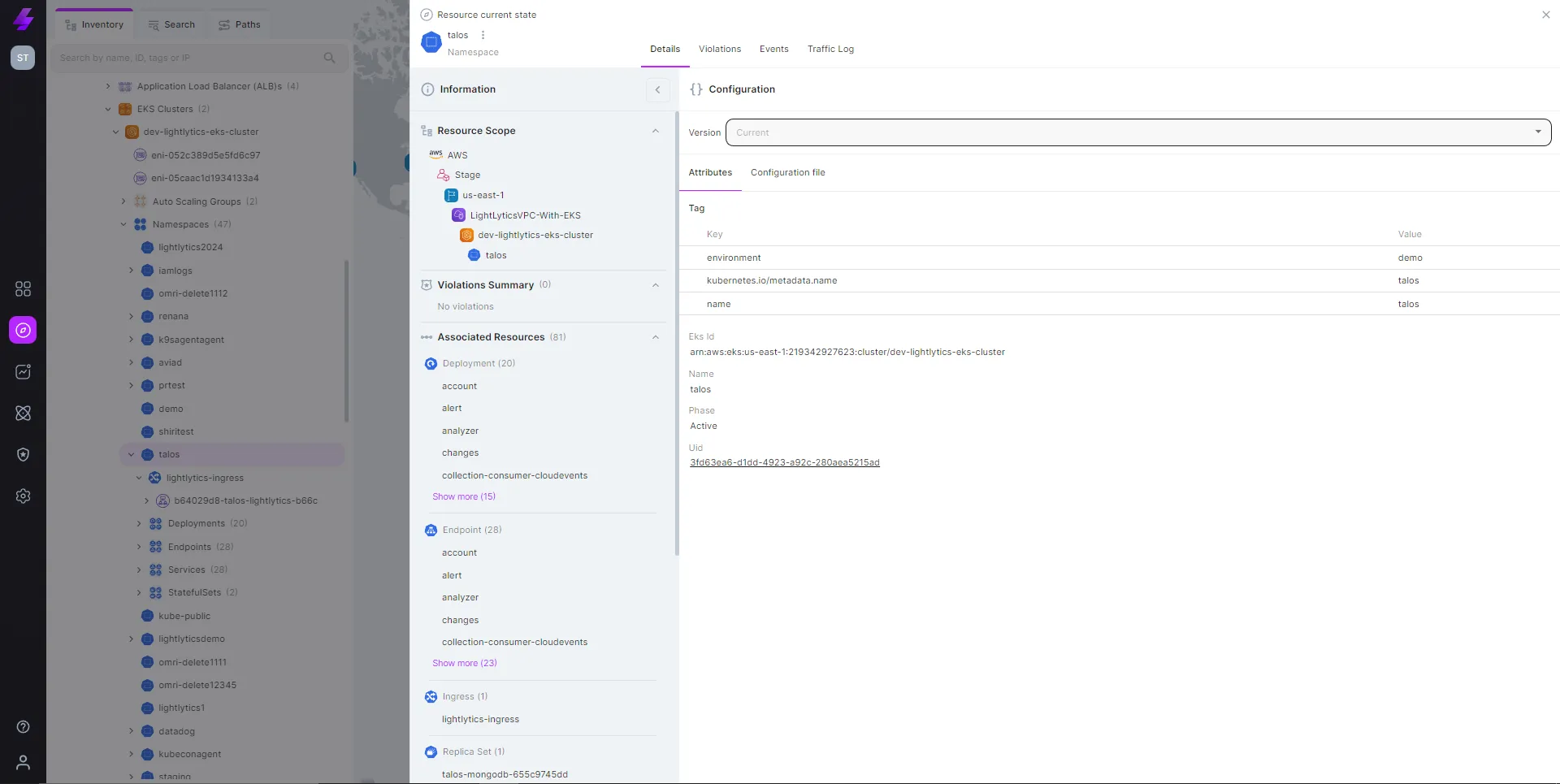
Easily understand your entire k8s posture and trouble shoot k8s connectivity
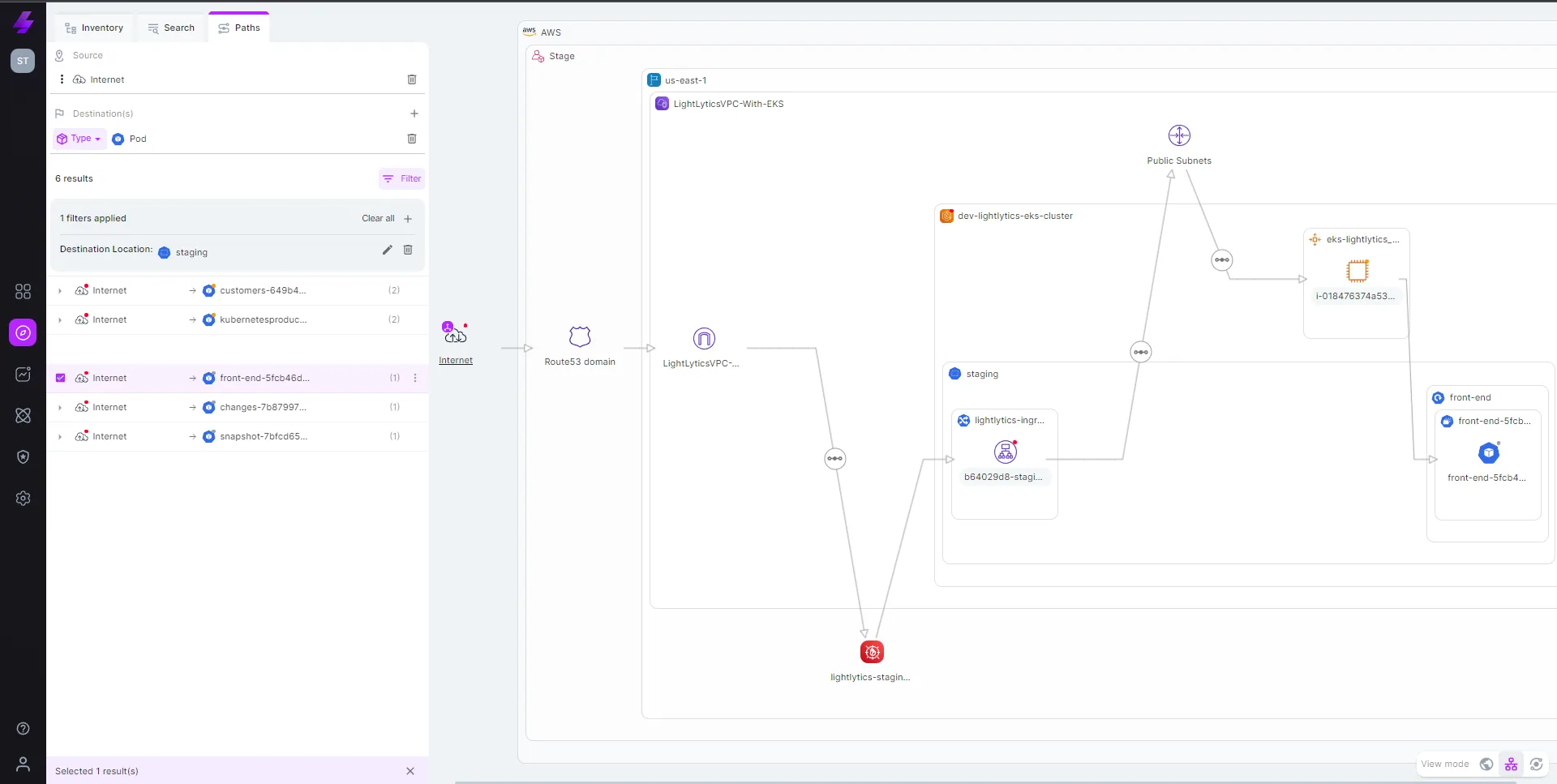
View which policies are allowed by PODs and how they areassumed, find the missing policies you need to set in order to meet newrequirements
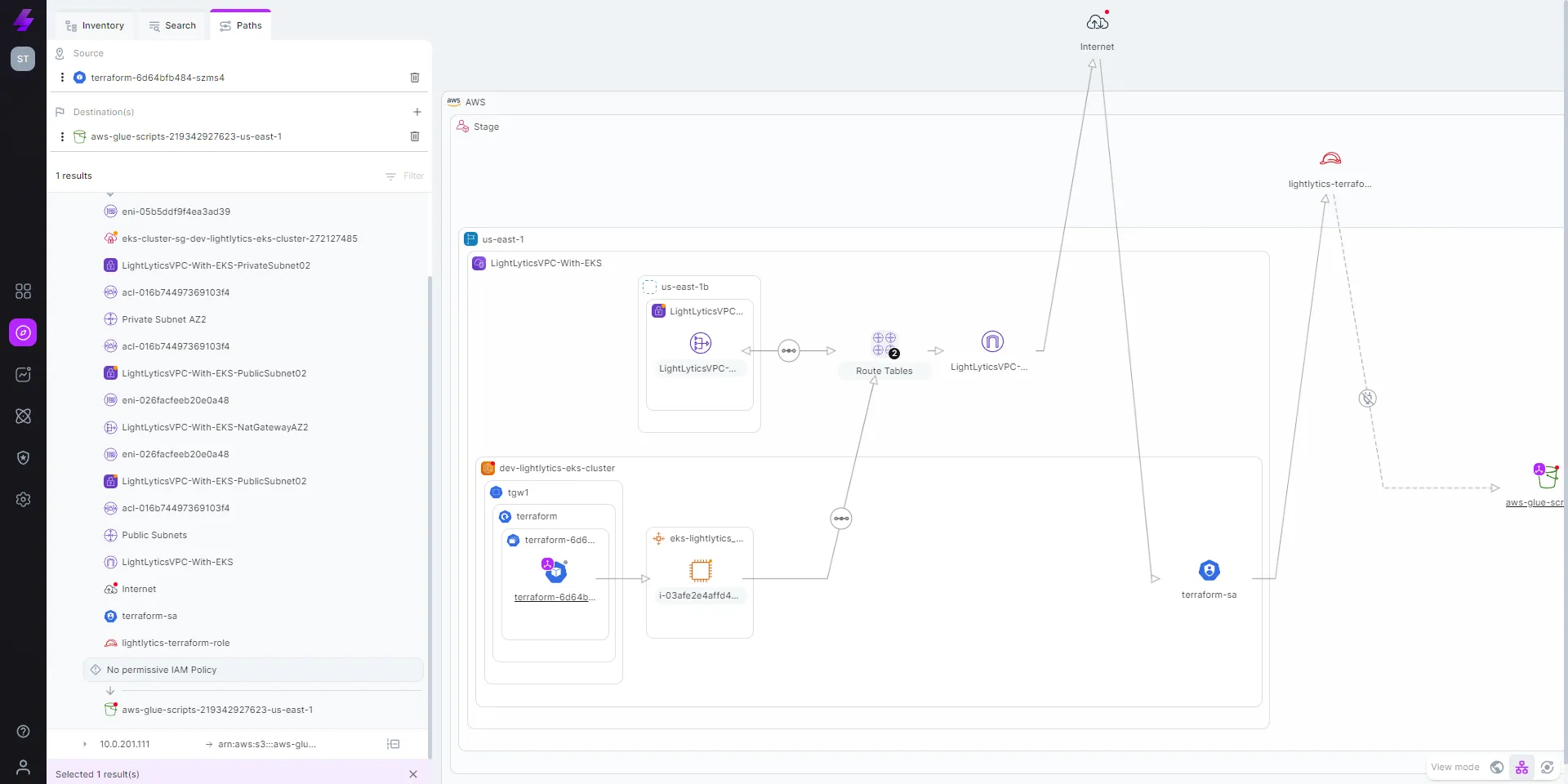
Get the entire picture by seeing activity related to pods
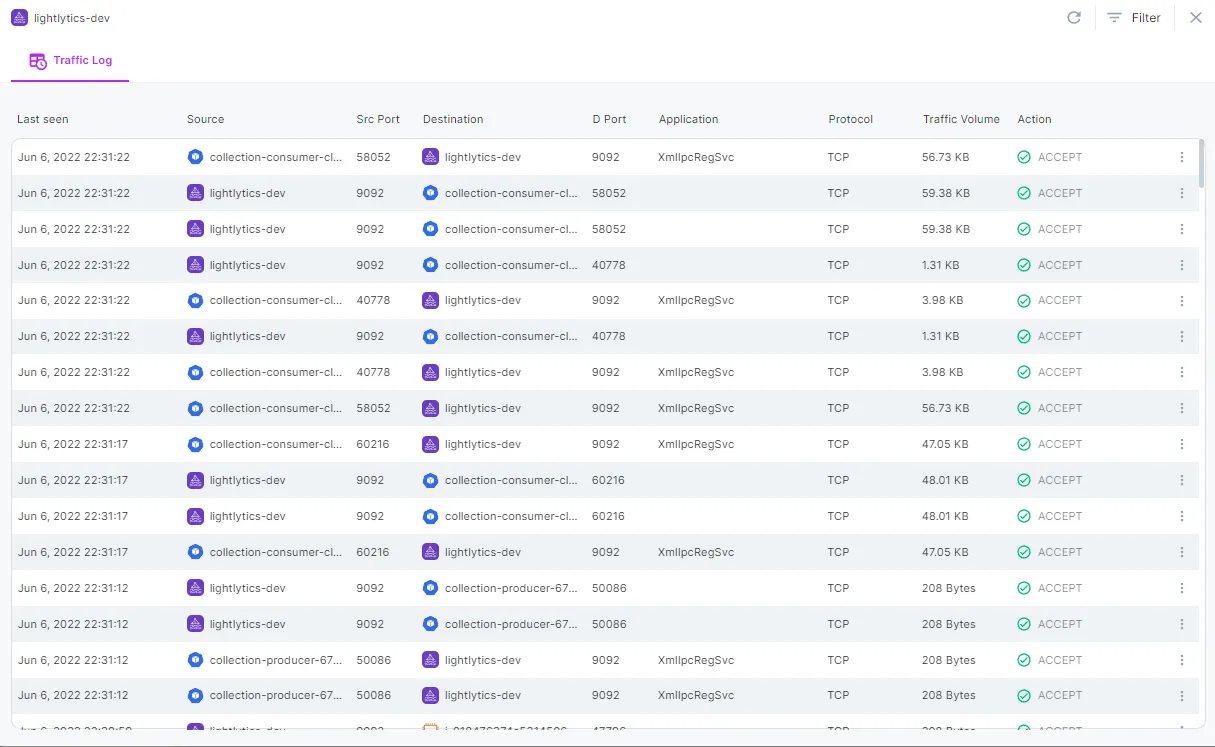
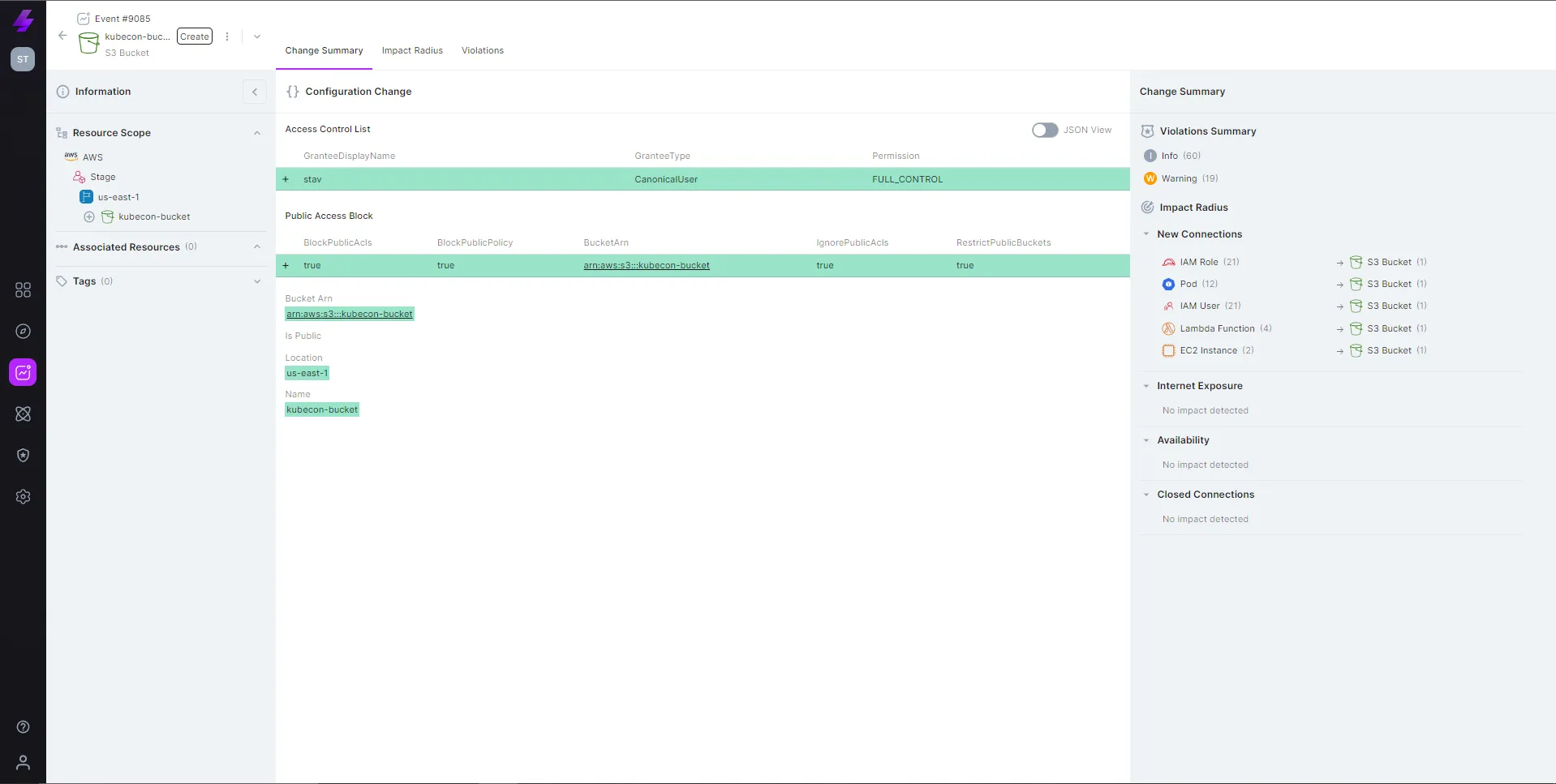
Keep track of all configuration changes and impacts between the cloud layer and the k8s layer.
Built-in, industry-best practice guardrails for k8s, and the ability to set community knowledge policies based on a company's unique needs.
Predefined Guardrails for you Kubernetes workloads
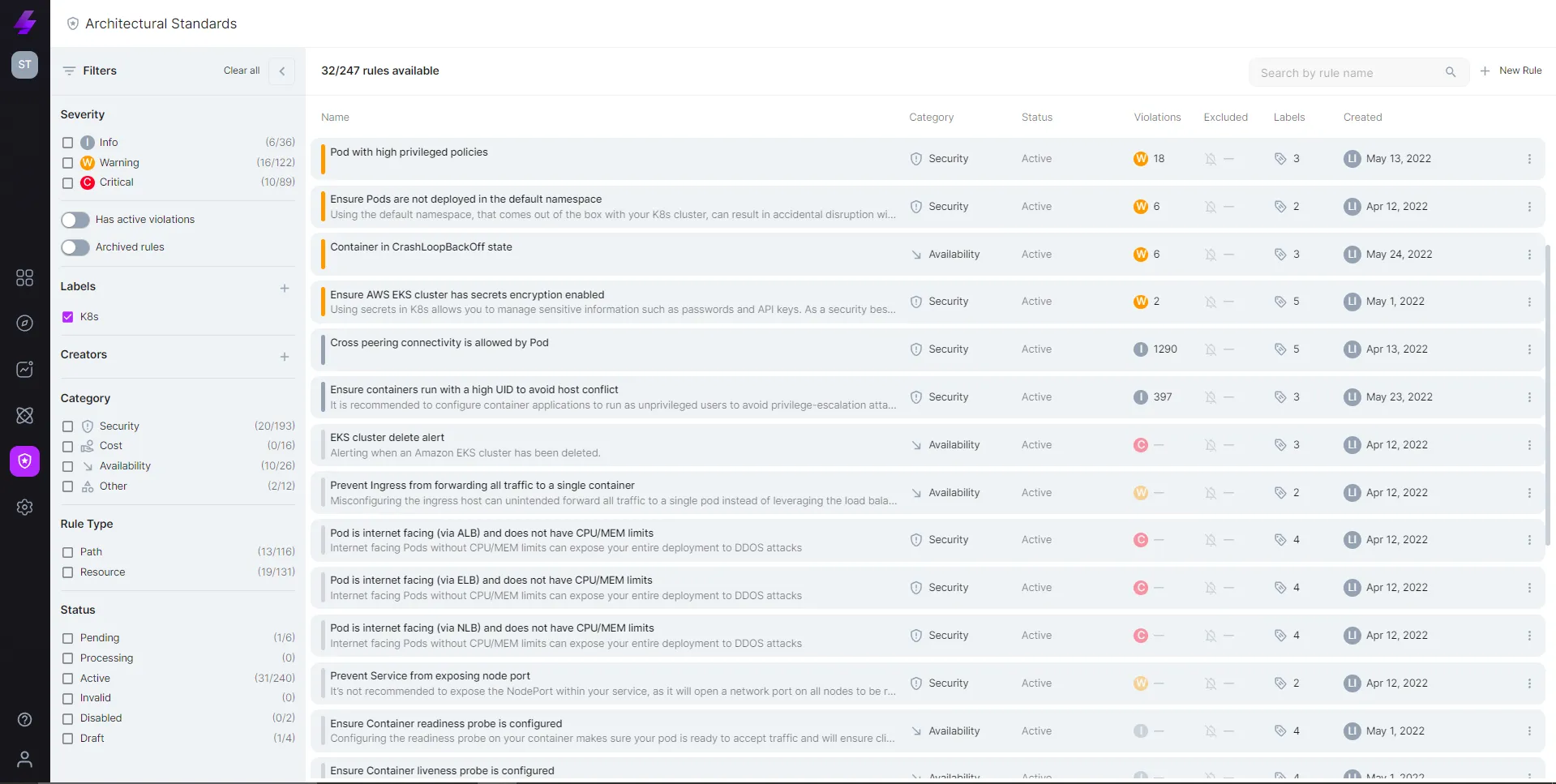
Incorporate community knowledge into our system so that the collective experience of your team is checked against any change:
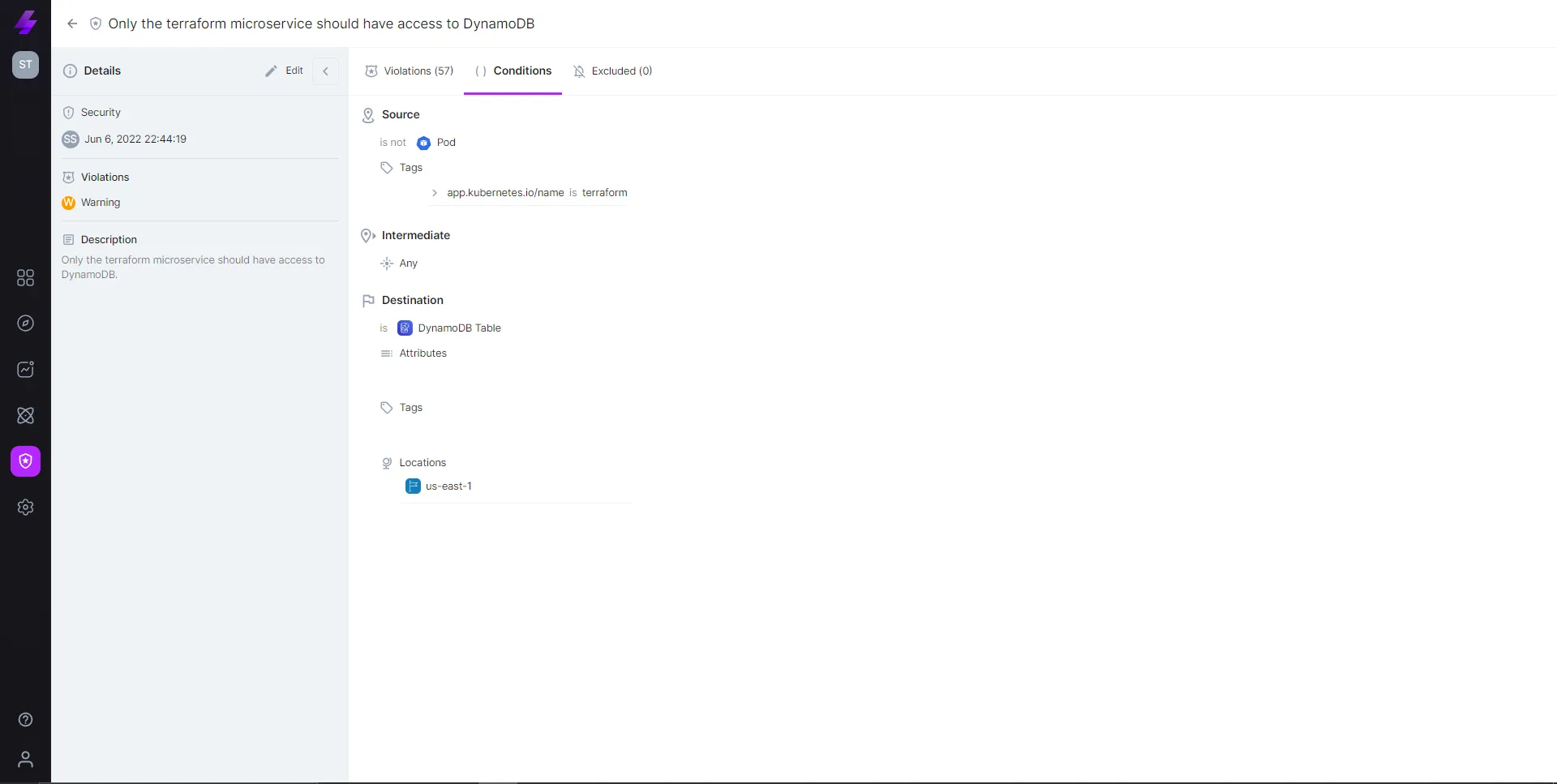
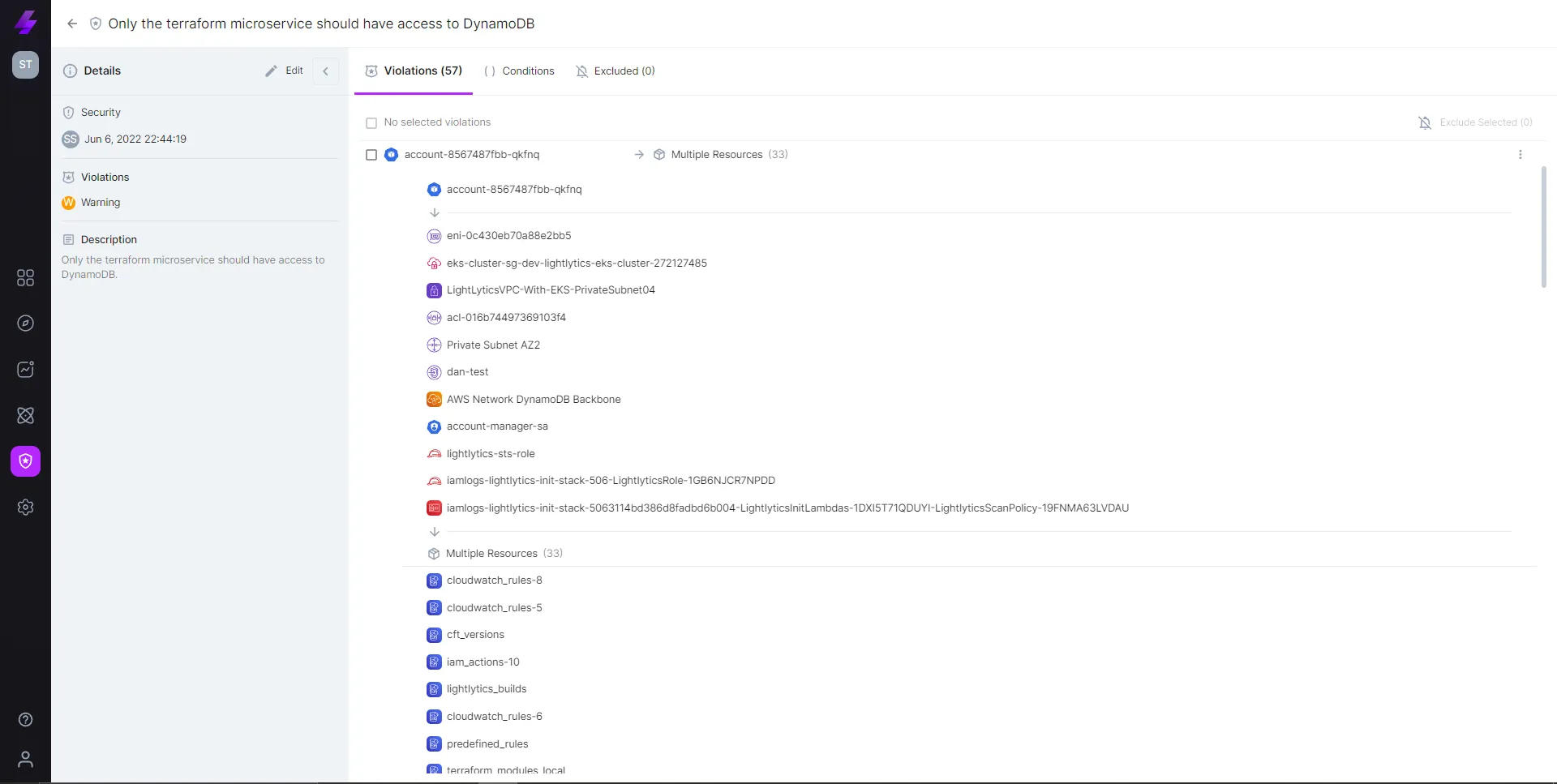
See Violations with the full context:
We will be at Kubecon Detroit October 24-27 in booth #S67 stop by to see how the magic works

Sign up for our Treemium offer! get 21 days for free and a tree planted in your name.
https://www.lightlytics.com/treemium
Stream.Security delivers the only cloud detection and response solution that SecOps teams can trust. Born in the cloud, Stream’s Cloud Twin solution enables real-time cloud threat and exposure modeling to accelerate response in today’s highly dynamic cloud enterprise environments. By using the Stream Security platform, SecOps teams gain unparalleled visibility and can pinpoint exposures and threats by understanding the past, present, and future of their cloud infrastructure. The AI-assisted platform helps to determine attack paths and blast radius across all elements of the cloud infrastructure to eliminate gaps accelerate MTTR by streamlining investigations, reducing knowledge gaps while maximizing team productivity and limiting burnout.
