
Like in many other domains, change is the only constant when it comes to cloud operations. Finding the right balance between speed and control becomes essential in high paced, large AWS environments where multiple changes get pushed on an hourly basis. To manage these dynamic environments, we all need to be able to provision cloud resources quickly for your applications. At the same time, we need to follow regulatory, security, and operational best practices, depending on our industry.
Keeping the tabs on configuration changes, monitoring for security & compliance, auditing and reporting and resource optimization are all daily tasks for most cloud teams managing sizeable AWS environments today.
These operational tasks can be done with the native tools provided by AWS, or by using third party tools. In this post, we’ll introduce AWS Config, a native change management tool from AWS, and how your teams can use it. We’ll also share what we believe is a more capable, scalable and cost-effective alternative: using the Stream Security platform for AWS change management at scale.
AWS Config is a fully managed service by AWS that provides monitoring and assessment of AWS resource configurations to support compliance auditing, change management and troubleshooting, with resource histories and comparison of historical configurations against planned configurations.
Although AWS Config is a native AWS tool, it is not included in the base platform subscription. It is an additional cost that’s billed based on consumption. The billed cost of AWS Config for your organization depends on multiple consumption parameters including:
It's also worth noting that if you use AWS Config in conjunction with other AWS services, you may be charged for those additional services as well. For example, if you use AWS Config with Amazon Simple Notification Service (SNS) to send notifications, you will be charged for AWS Config and SNS usage. You can view the pricing for this service on the AWS Config web page.
AWS Config keeps track of the changes to your resources (aka the what – what did we change?) by invoking the Describe or the List API call for each monitored resource in your AWS account.
For example, removing an egress rule from a VPC security group causes AWS Config to invoke a “Describe API call” on the security group. AWS Config then invokes a Describe API call on all of the instances associated with the security group. The updated configurations of the security group (the resource) and of each instance (the related resources) are recorded as configuration items and delivered in a configuration stream to an Amazon S3 bucket.
Resource Timeline view:
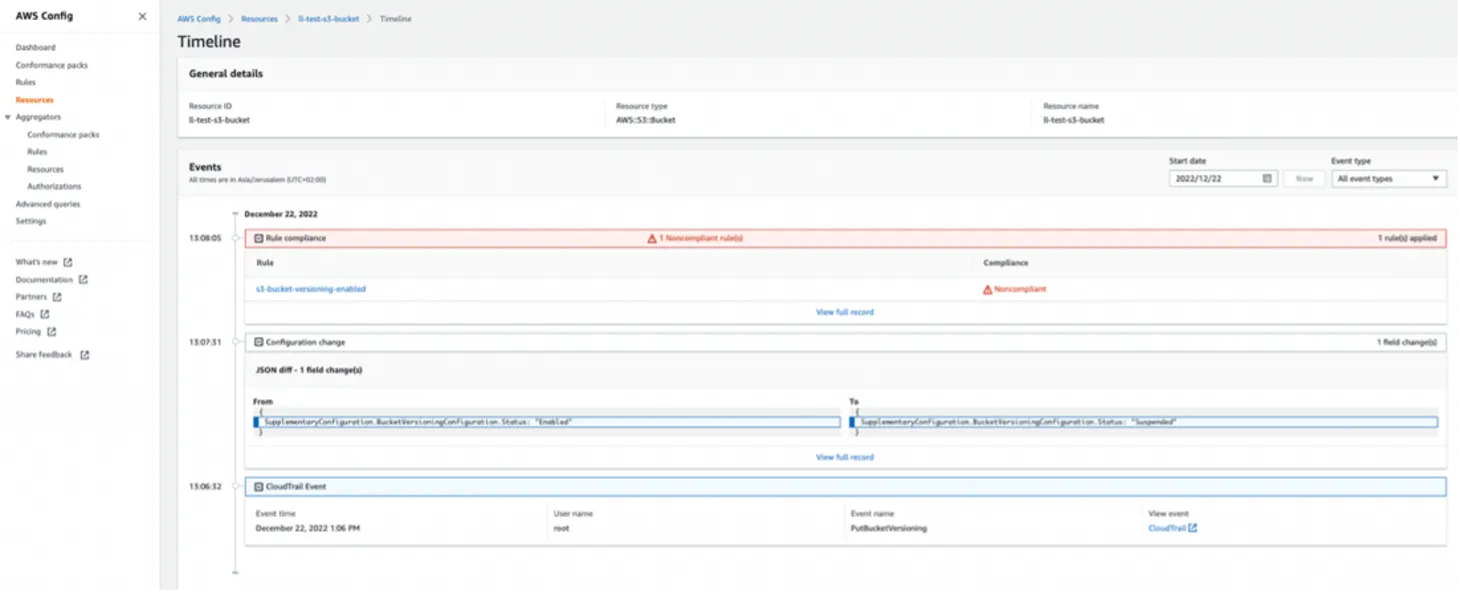
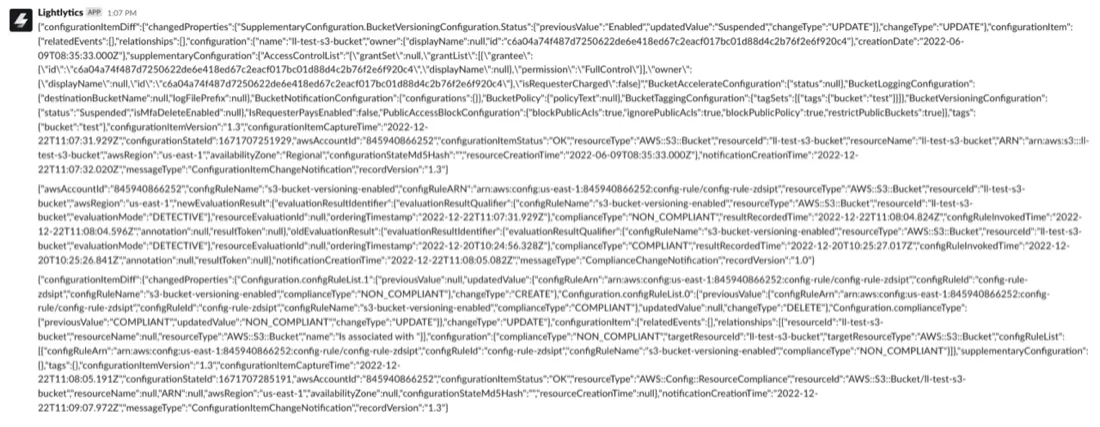
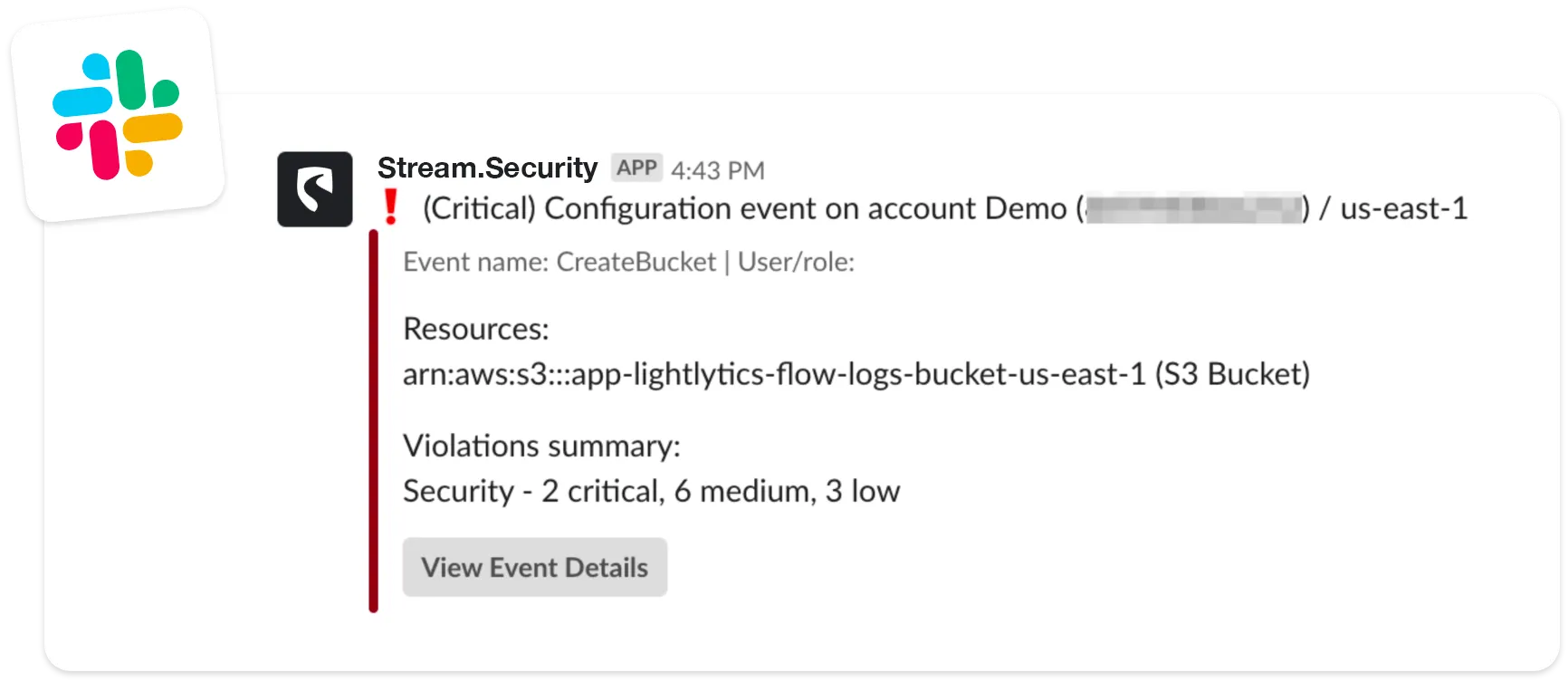
View of a configuration change in JSON format via SNS topic (Integrated with Slack):
Using AWS Config conformance rules, you can continuously evaluate your AWS resource configurations for desired settings. Depending on the rule, AWS Config evaluates your resources either in response to configuration changes or periodically. Each rule is associated with an AWS Lambda function, which contains the evaluation logic for the rule. When AWS Config evaluates your resources, it invokes the rule's AWS Lambda function. The function returns the compliance status of the evaluated resources. If a resource violates the conditions of a rule, AWS Config flags the resource and the rule as non-compliant. So in simple terms, all checks throw a pass (compliant) or fail (non-compliant) flag as a result.
When the compliance status of a resource changes, AWS Config sends a notification to your Amazon SNS topic.
AWS Config rules page view:
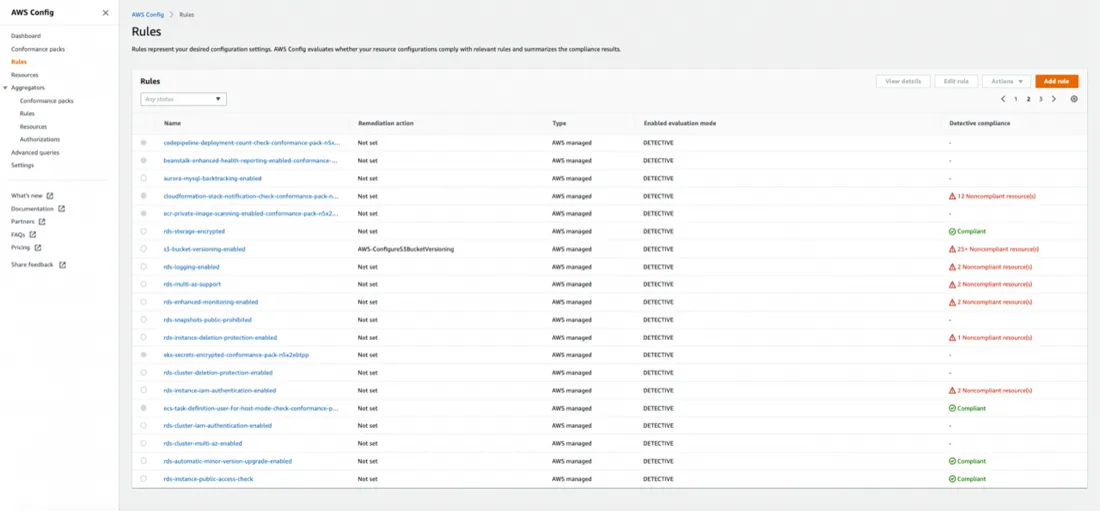
The capabilities listed above enable compliance auditing, security analysis, resource change tracking, and troubleshooting, and AWS Config can be a one-stop shop AWS change monitoring solution for small environments.
Yet, AWS Config comes with limitations including:
In customer reviews on G2, AWS Config customers called out (as of 2023-01-04):
These limitations with AWS Config are exactly why we believe your teams can benefit from a more capable, scalable and cost-effective solution with Stream Security.
Stream Security provides a single collaborative solution for all teams who work on managing AWS changes. This helps teams identify and fix incidents caused by misconfigurations in minutes, investigate security incidents more efficiently and reduce point tools and cost for AWS environments.
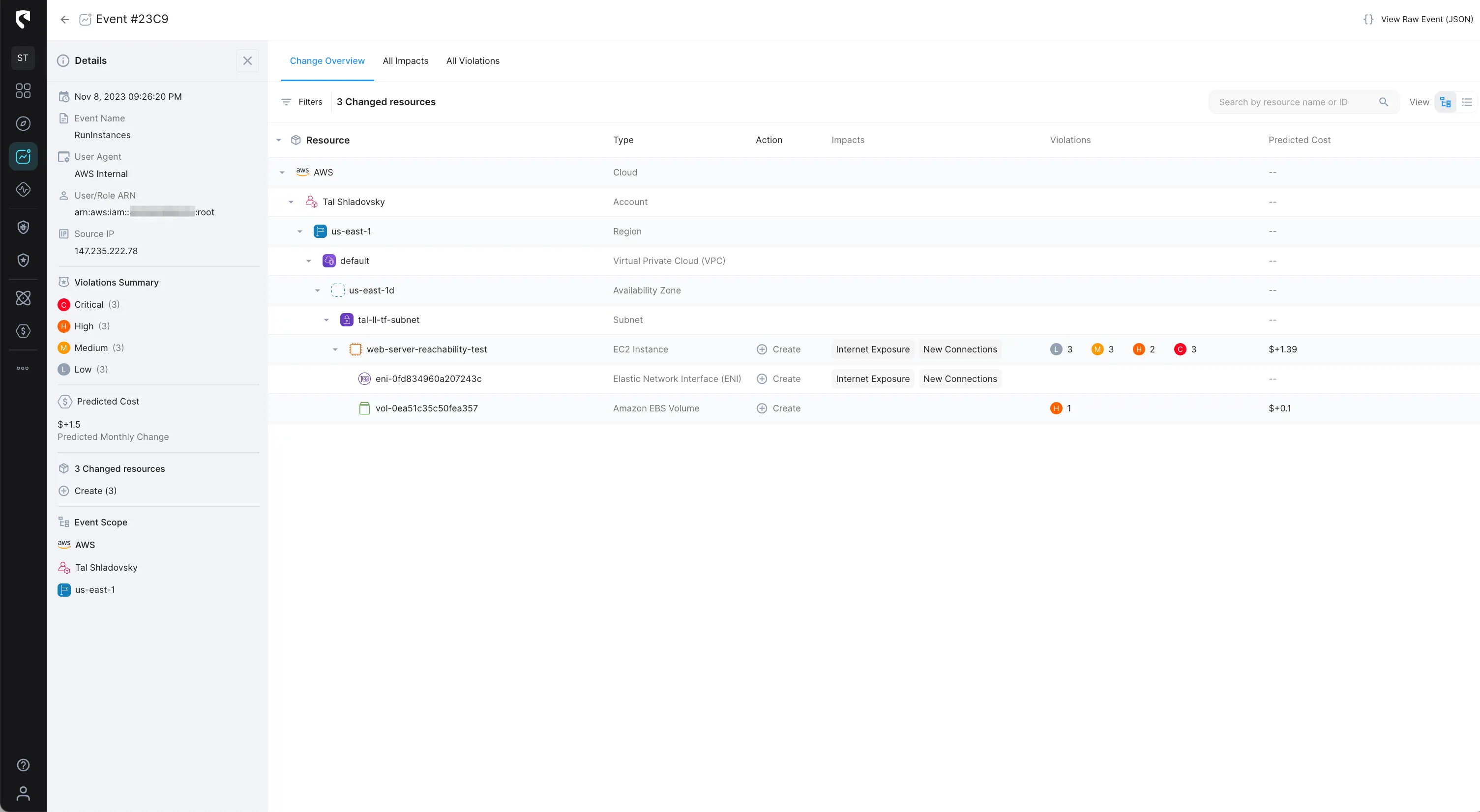
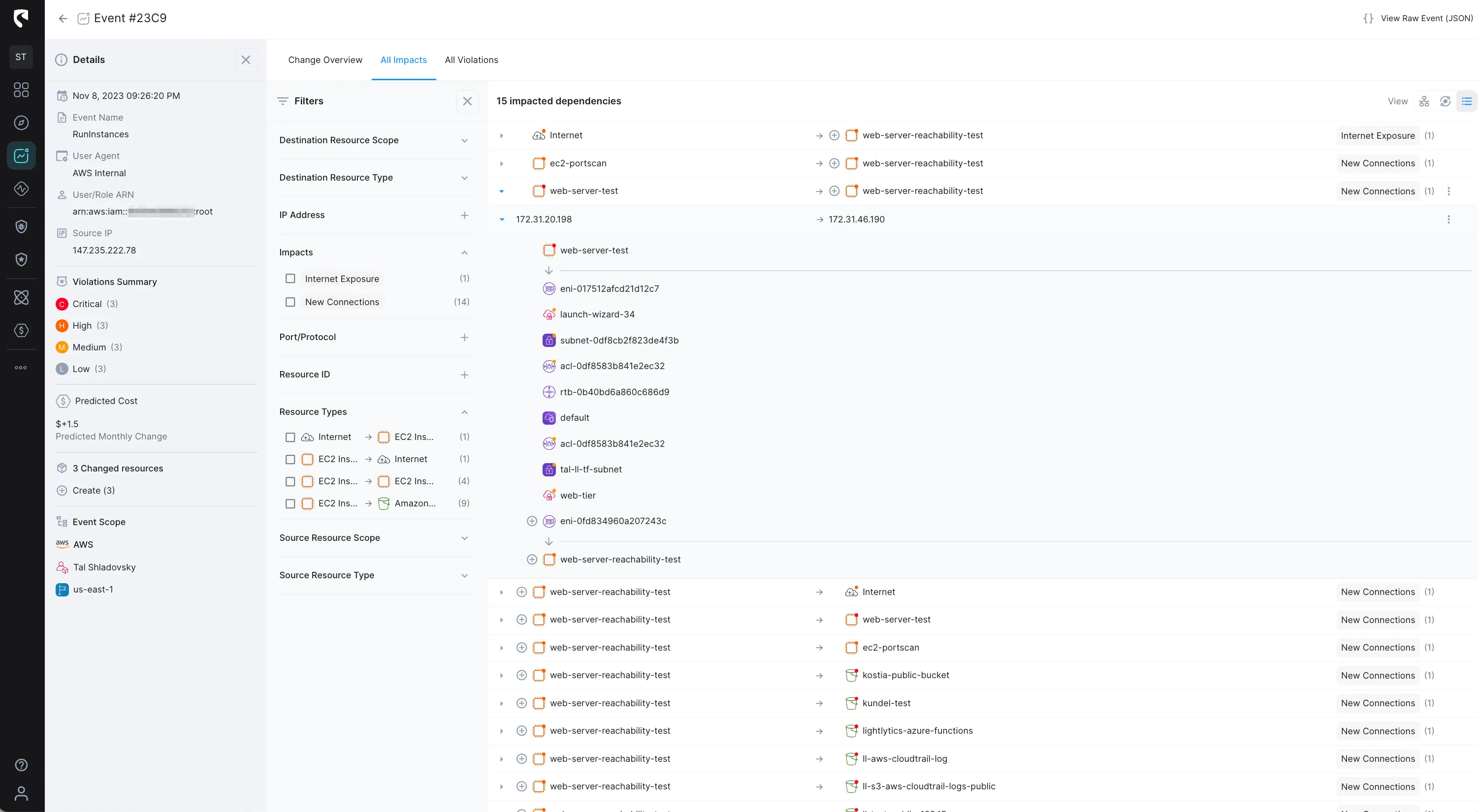
Upon connecting your AWS account to Stream, Stream will scan your cloud environment configurations across all the cloud-native stack, up to the data-plane layer, with the API-first, agent-less approach. This initial scan results in a real-time, deterministic mathematical model that represents your AWS environment across accounts, regions and availability zones. We call this the CloudTwin!
The CloudTwin engine dynamically correlates the dependencies between services and infrastructure by simulating the environment and all its dependencies in code.
Unlike other tools that scan your entire cloud configuration periodically to understand what has changed, Stream consumes cloud events in real-time. The result is an accurate real-time representation of your environment, at any given time.
Let's review Stream's capabilities and how they can provide a good alternative to AWS Config for you:
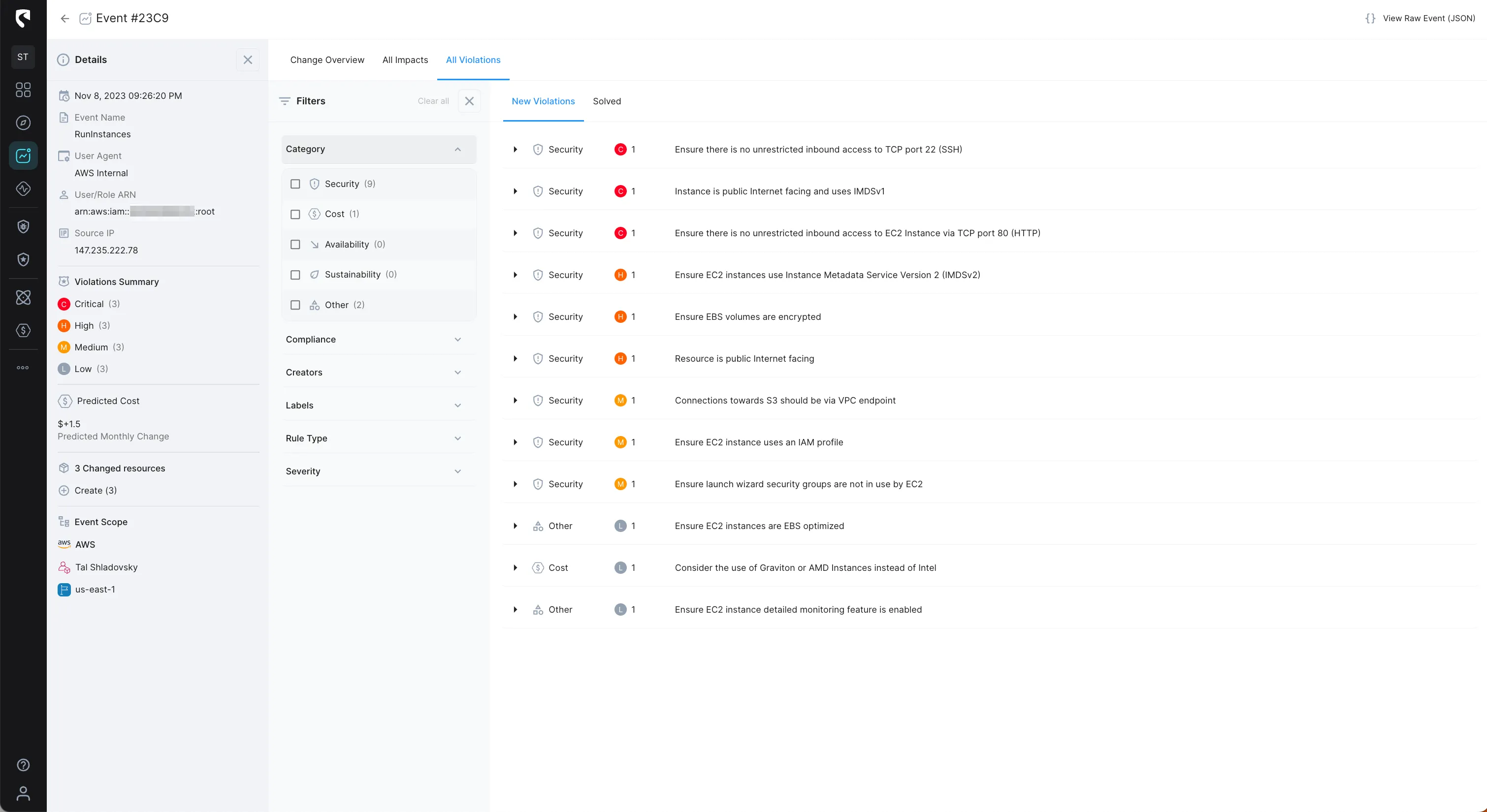
Stream Security's Architectural Standards enable cloud operation teams to incorporate their tribal knowledge into our platform in the form of predefined and custom rules to ensure the collective experience of the team is taken into consideration for any configuration change at any time.
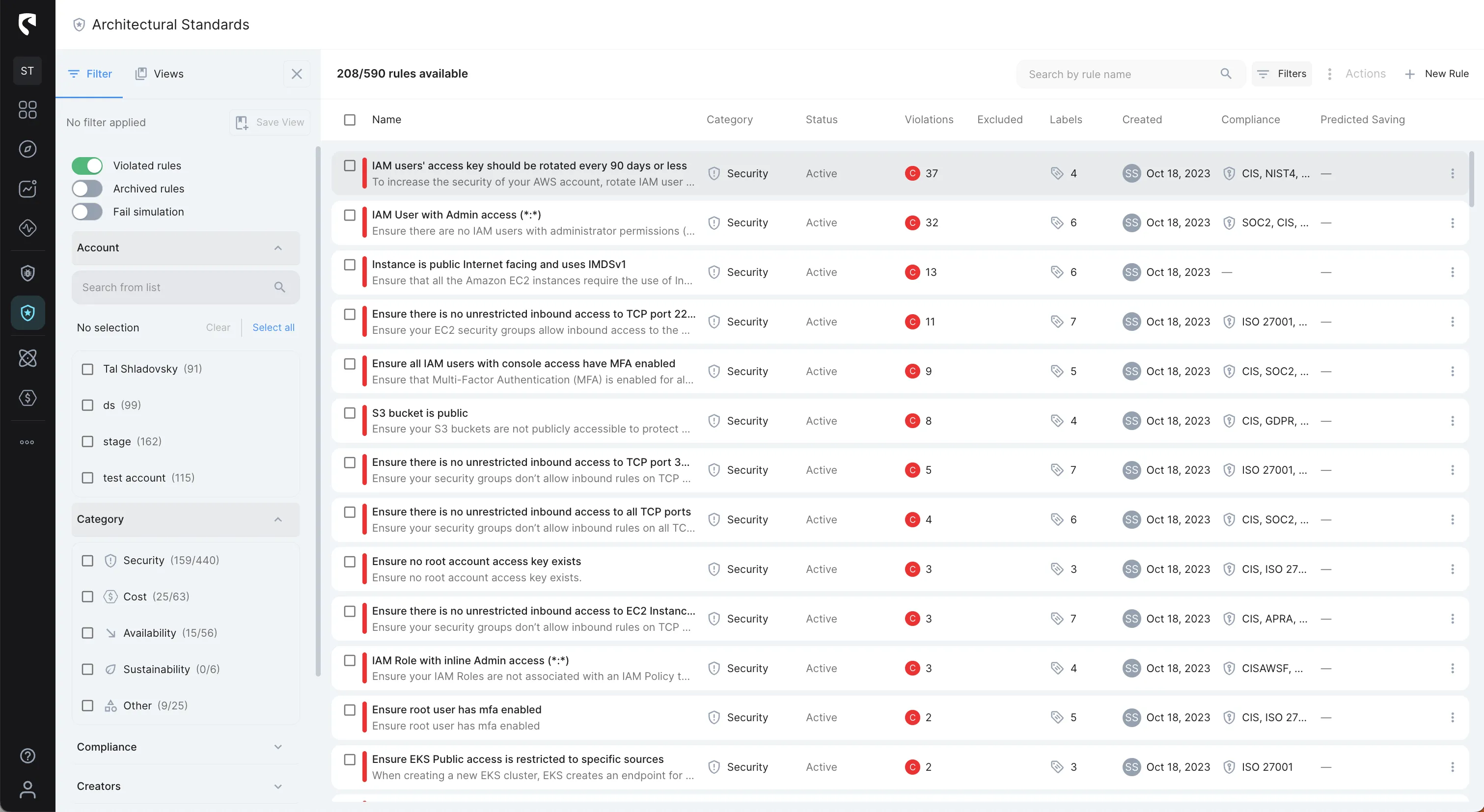
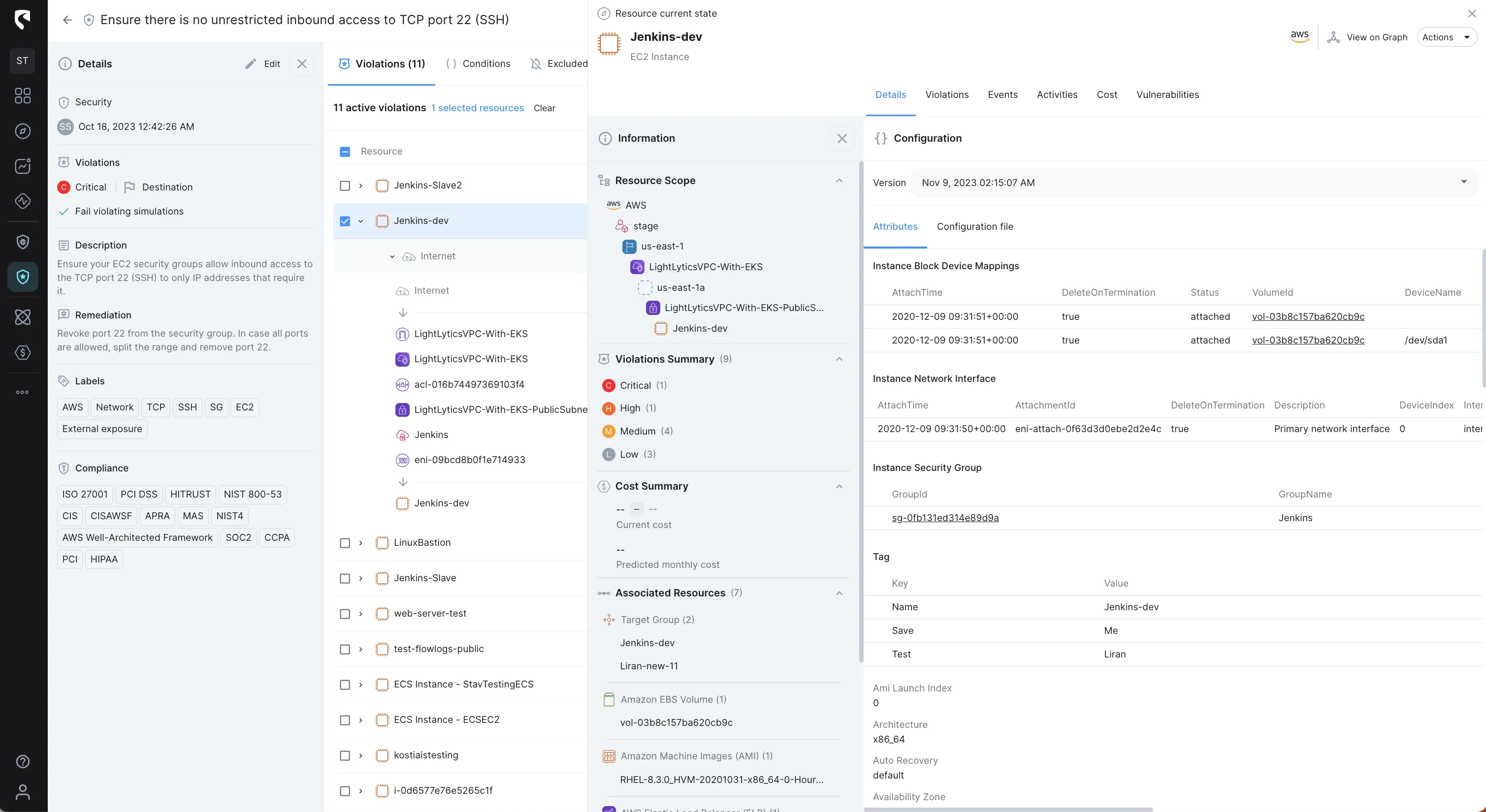
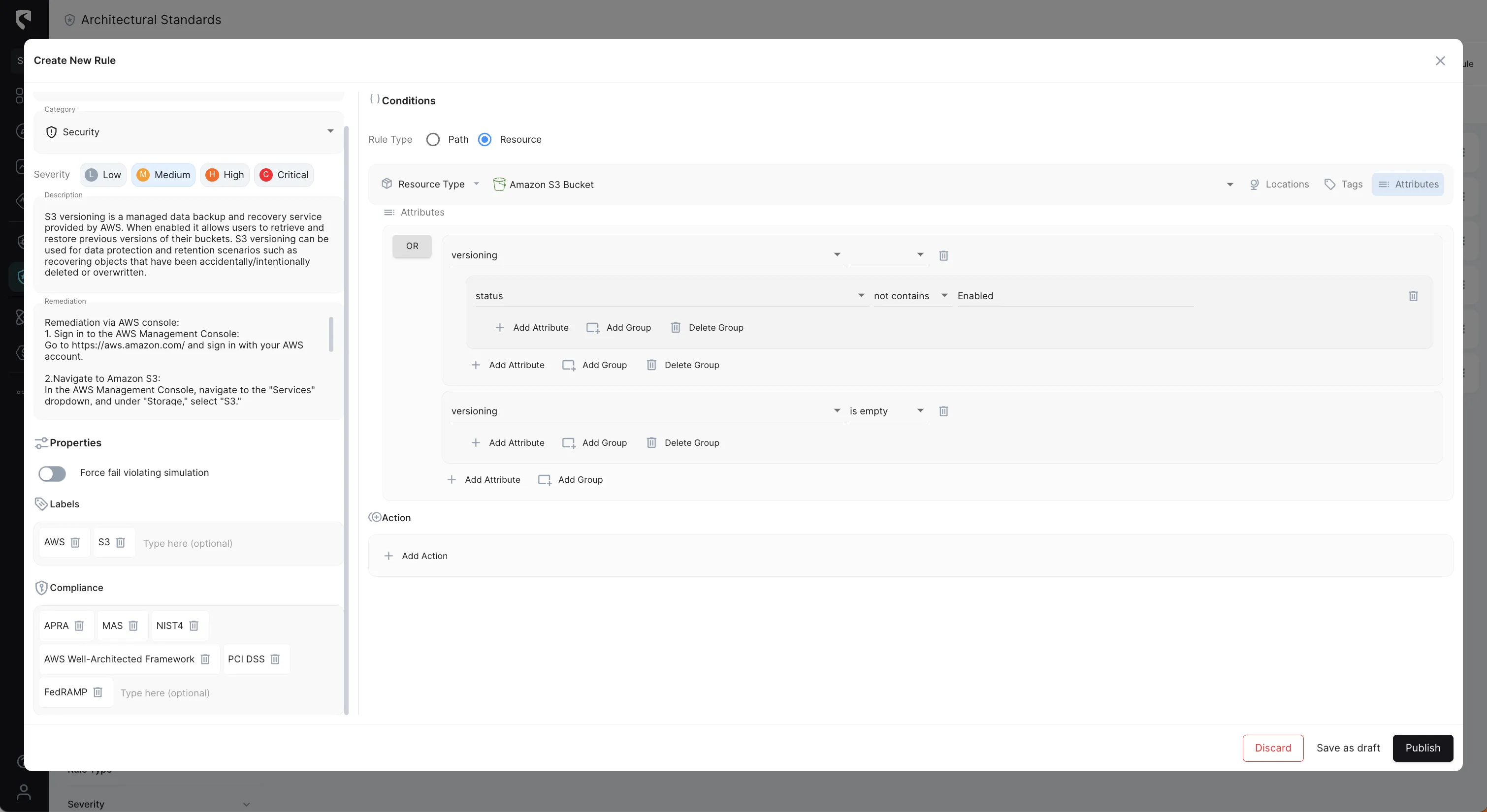
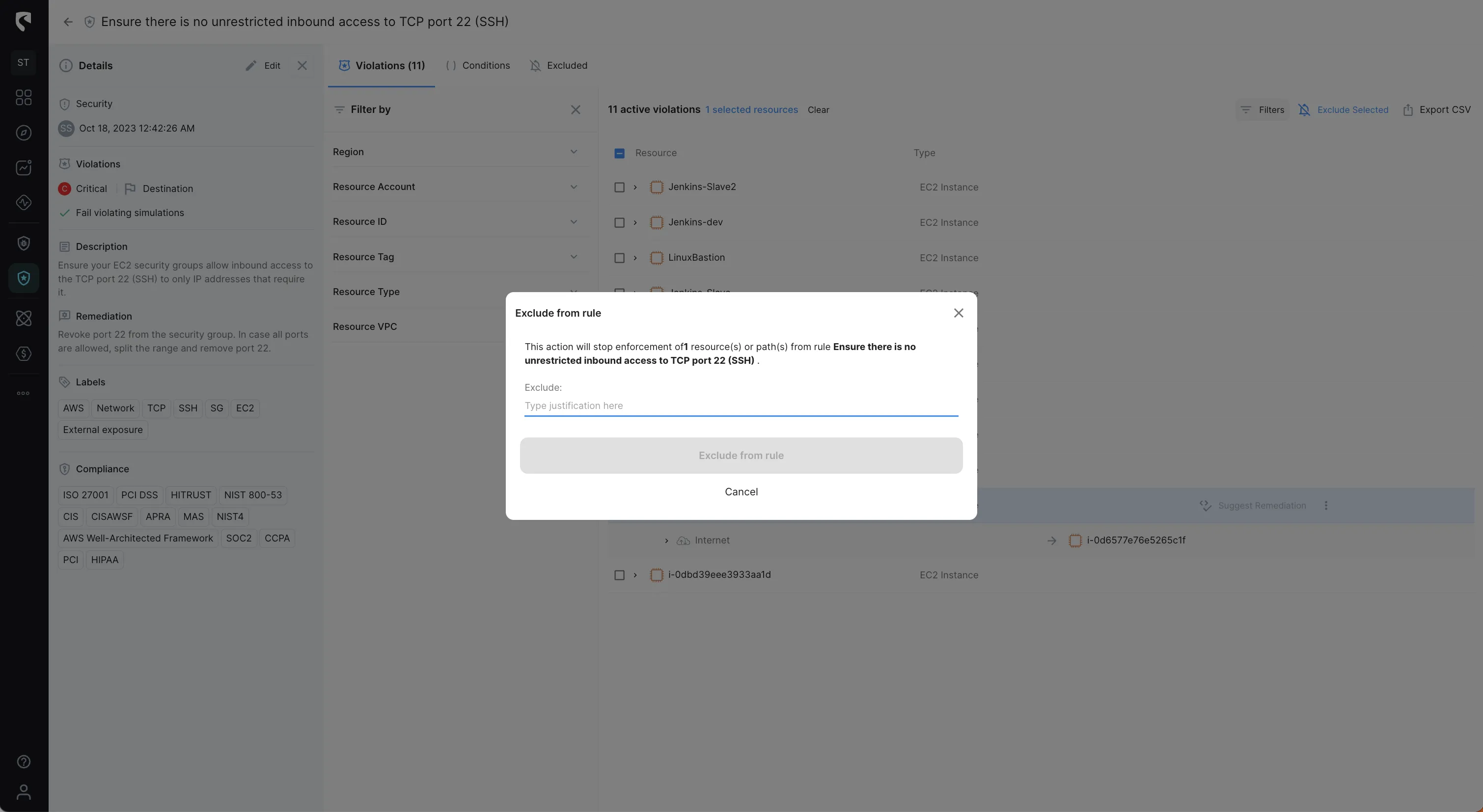
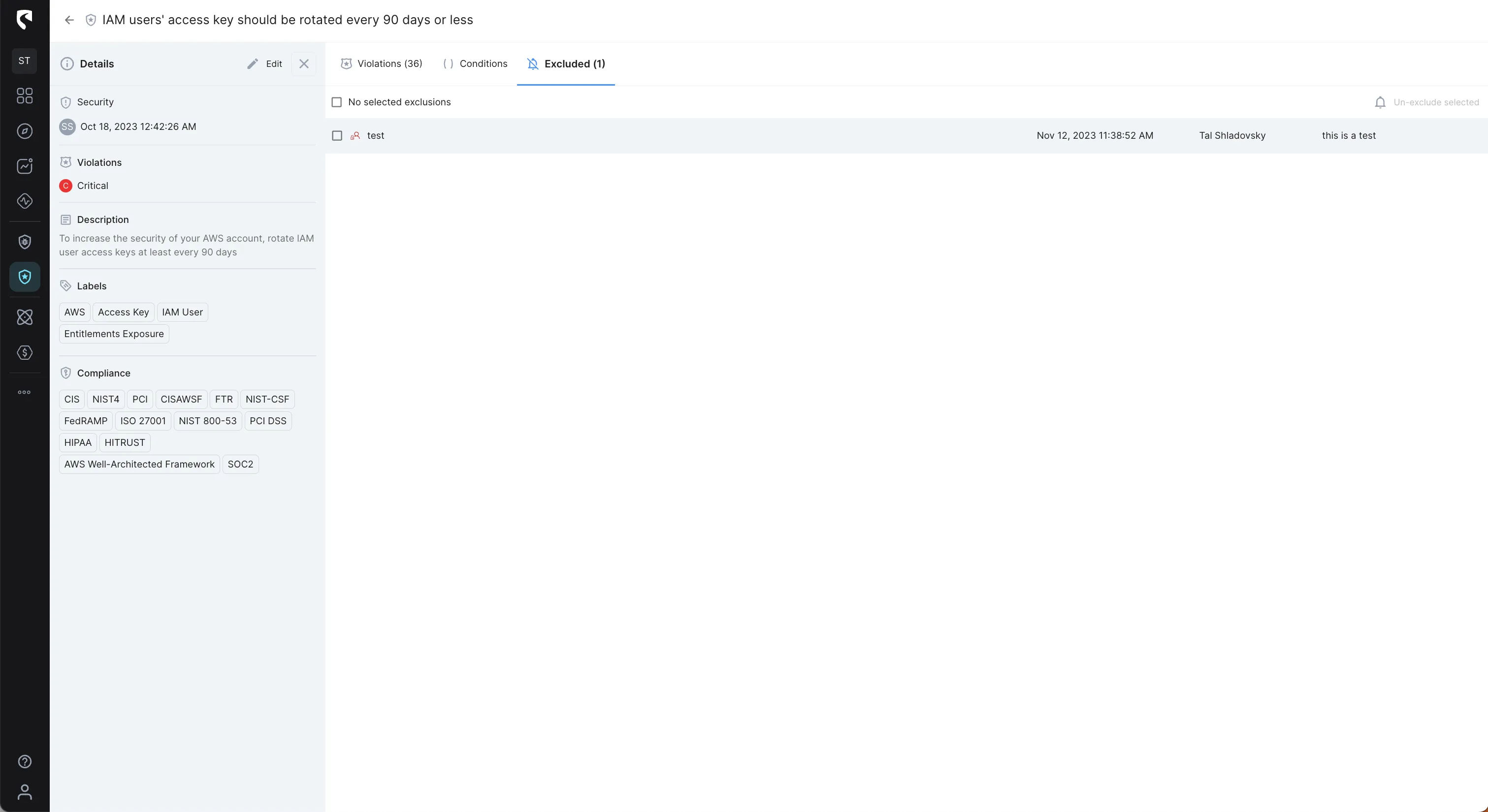
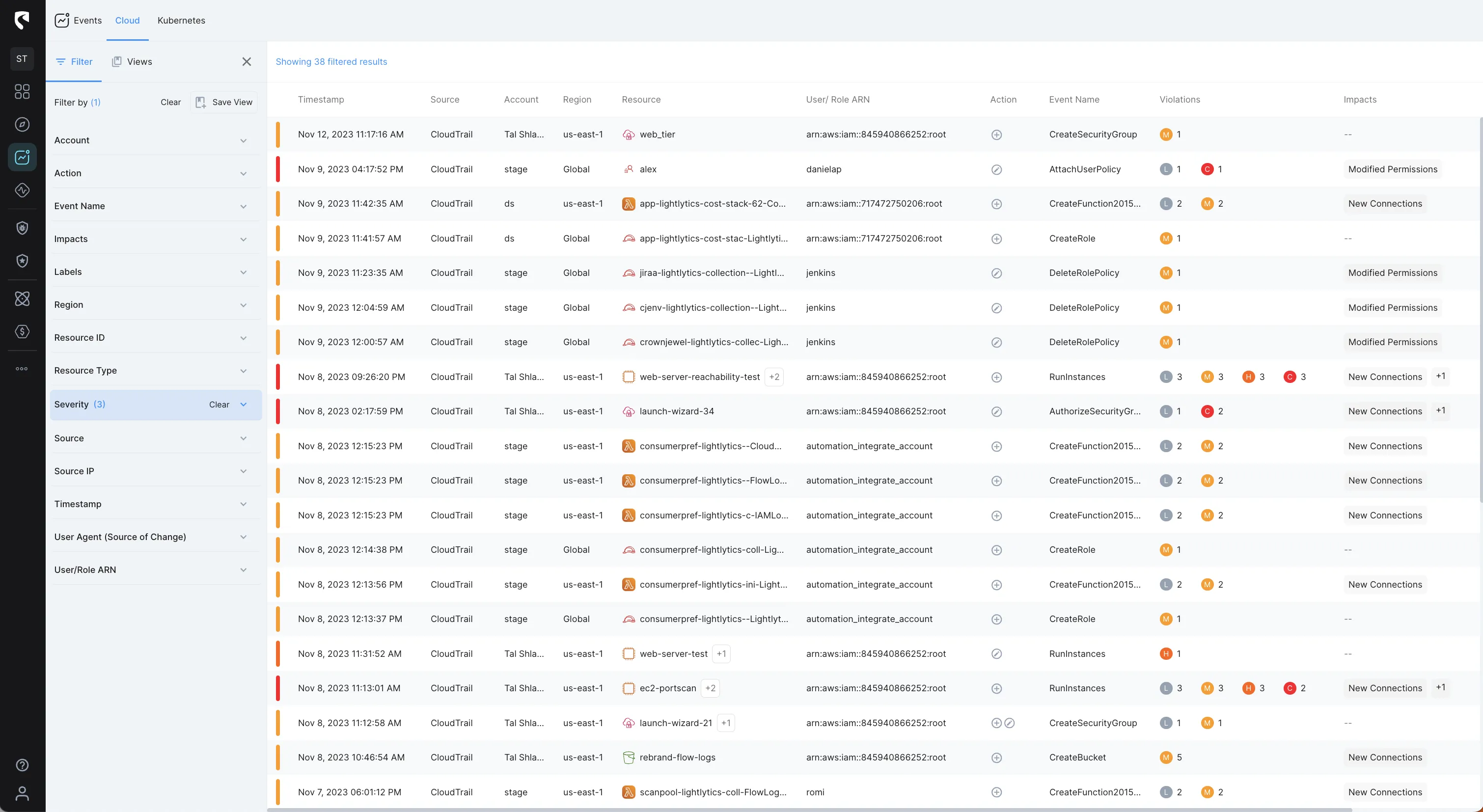
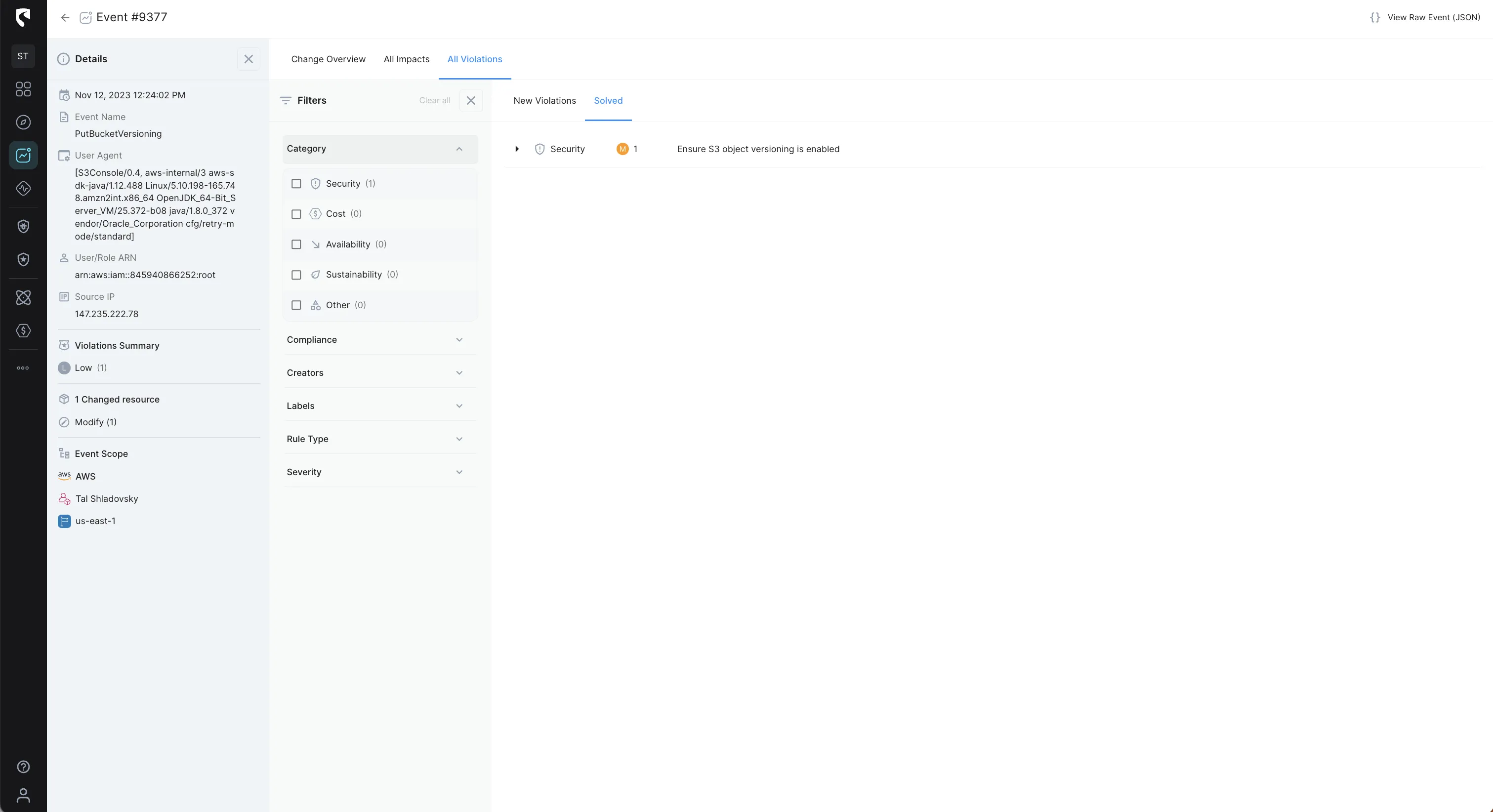
Stream Security's Events tracks cloud configuration changes with exact, real-time model of your cloud environment and lets you get notified of changes in real-time to review changes with complete context and impact analysis.
With Events you can basically track the Who, What, Where, and When of every activity in your cloud environment.
AWS Config offers basic capabilities for small AWS environments, but has limitations when it comes to complex and dynamic environments. We're obviously biased, and we believe your AWS environments require a more capable, scalable and cost-effective solution!
All in all, your teams can cover:
in your dynamic AWS environments using Stream Security. We work with innovative customers including Sony, Kaltura, Neuron and many others to save operational effort and license cost in AWS environments.
As a sanity check, try answering these questions in your environment with AWS Config today:
We’d love to hear about how you handle AWS changes today and how we can help your team scale.
Get started with Stream Security for Free or book a demo with one of our cloud experts to hear more.
Stream.Security delivers the only cloud detection and response solution that SecOps teams can trust. Born in the cloud, Stream’s Cloud Twin solution enables real-time cloud threat and exposure modeling to accelerate response in today’s highly dynamic cloud enterprise environments. By using the Stream Security platform, SecOps teams gain unparalleled visibility and can pinpoint exposures and threats by understanding the past, present, and future of their cloud infrastructure. The AI-assisted platform helps to determine attack paths and blast radius across all elements of the cloud infrastructure to eliminate gaps accelerate MTTR by streamlining investigations, reducing knowledge gaps while maximizing team productivity and limiting burnout.
