
As organizations increasingly migrate to the cloud, the landscape of cybersecurity evolves, presenting new and complex challenges for security teams. The dynamic nature of cloud environments, coupled with the scale and sophistication of potential threats, demands a proactive and context-driven approach to threat detection. Traditional security measures often fall short, requiring security teams to adapt and develop strategies that can effectively identify, prioritize, and neutralize threats in the cloud. In this blog, we’ll review threat detection challenges in the cloud, and how Stream Security can help overcome these challenges.
To handle threats in the cloud, security teams need to understand the entire context of the cloud to:
Given the complex and interconnected nature of cloud environments, understanding the full context behind a potential threat is crucial for effective detection and response. This is where advanced tools come into play, offering the ability to not only identify and prioritize threats but also to deeply analyze and mitigate them. Stream Security's Cloud Detection and Response (CDR) solution exemplifies this approach, providing the necessary context and real-time insights that security teams need to handle cloud-based threats efficiently and effectively.
Stream Security’s cloud threat detection and response (CDR) solution leverage its revolutionary CloudTwin technology, provides a precise and constantly updated model of the cloud environment by continuously tracking behavior and configuration changes out of cloud logs. With dynamic algorithms at work, every alteration triggers a thorough analysis that delivers an accurate and comprehensive impact assessment on each change, and by that provides actionable results to detect, triage, pinpoint and address threats in minutes.
Stream Security combines three cloud context dimensions:
To provide threat detection contextual information, Stream Security utilizes its built-in anomaly-detection engine to:
Stream Security's detection mechanism provides comprehensive monitoring and analysis across cloud environments, focusing on both workloads and identities. By leveraging a blend of indicator-based and behavioral analytics, our system accurately identifies potential threats and anomalies, ensuring robust protection against diverse security risks.
Let’s review a threat detection investigation from end-to-end using Stream Security with the following example.
1. Alert Received: Anomalous Network Traffic
The security team is alerted to unusual network activity, indicating potential suspicious behavior within the cloud environment.
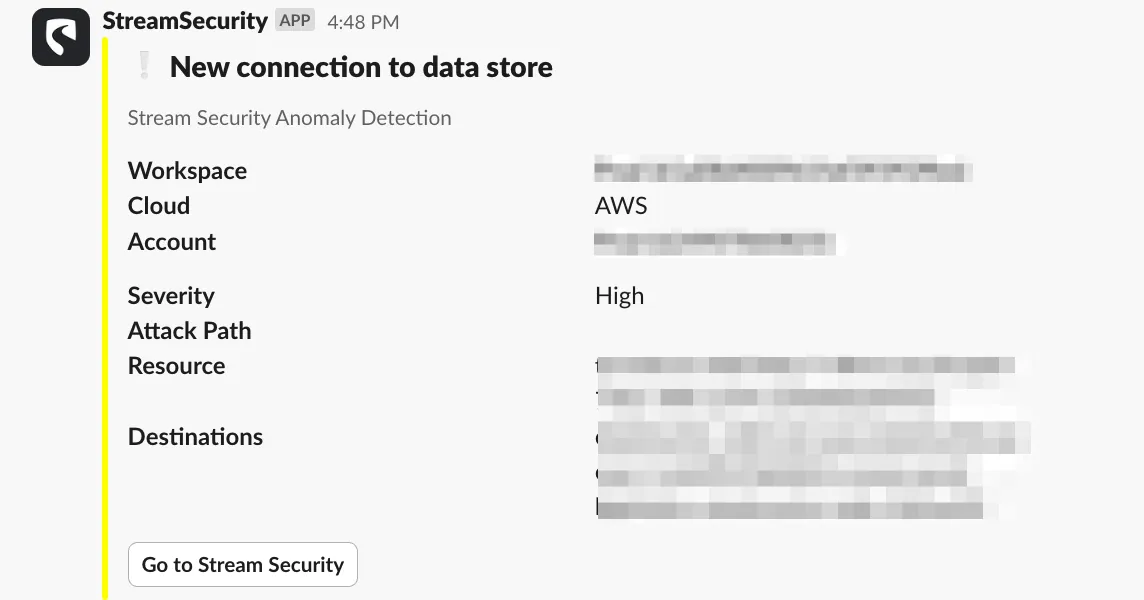
2. Identifying the Impacted EC2 Instance
Upon receiving the alert, the security team identifies that the anomalous traffic originates from a specific EC2 instance, pinpointing it as the affected asset requiring further investigation.
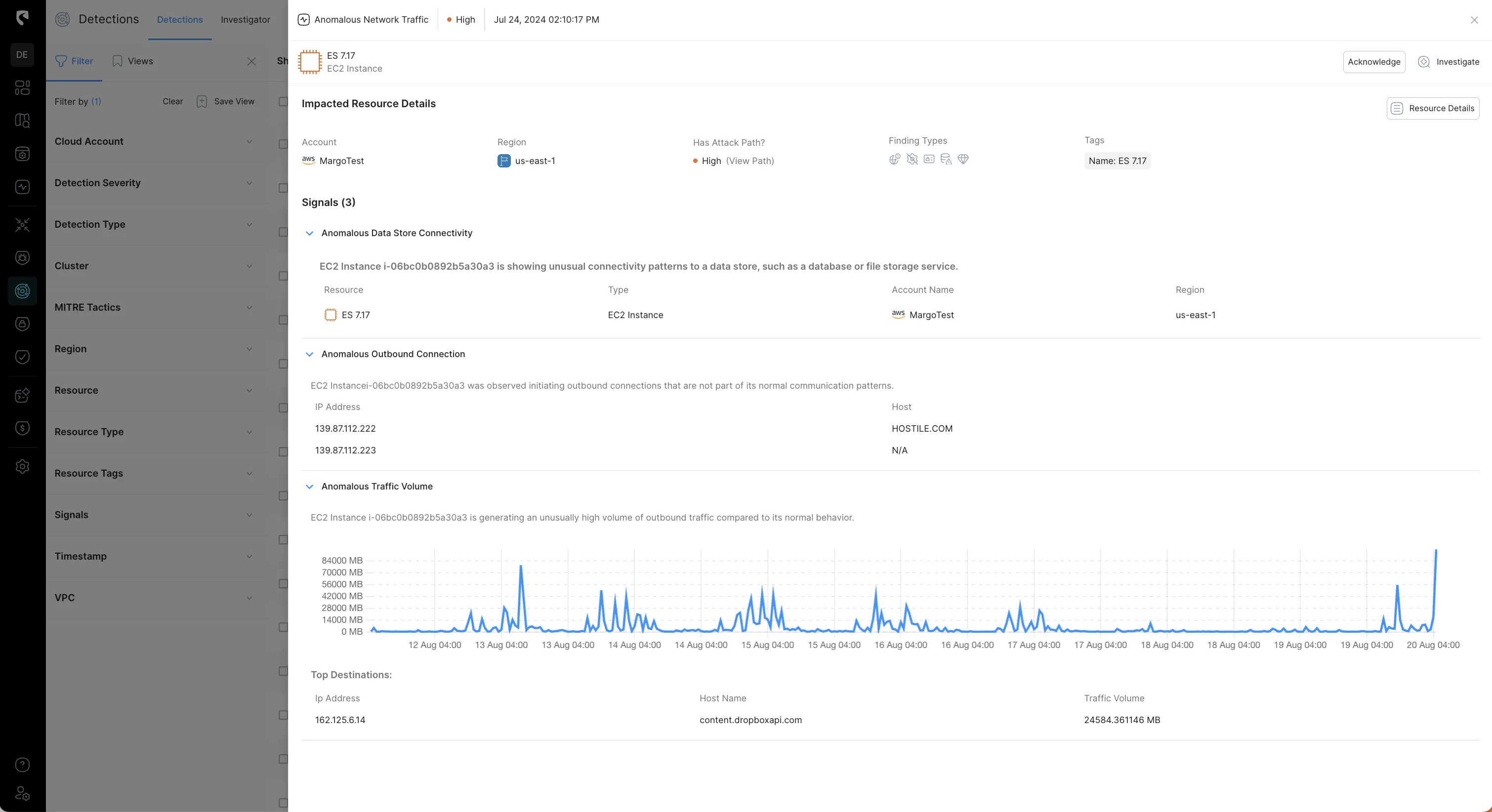
3. Analyzing Trigger Signals
The alert was triggered by three key indicators (signals):
- The EC2 instance exhibited unusual connectivity patterns to a data store, such as a database or file storage service.
- The instance initiated outbound connections that deviated from its normal communication behavior.
- There was an unusually high volume of outbound traffic compared to the instance's typical activity.
4. Initiating Further Investigation
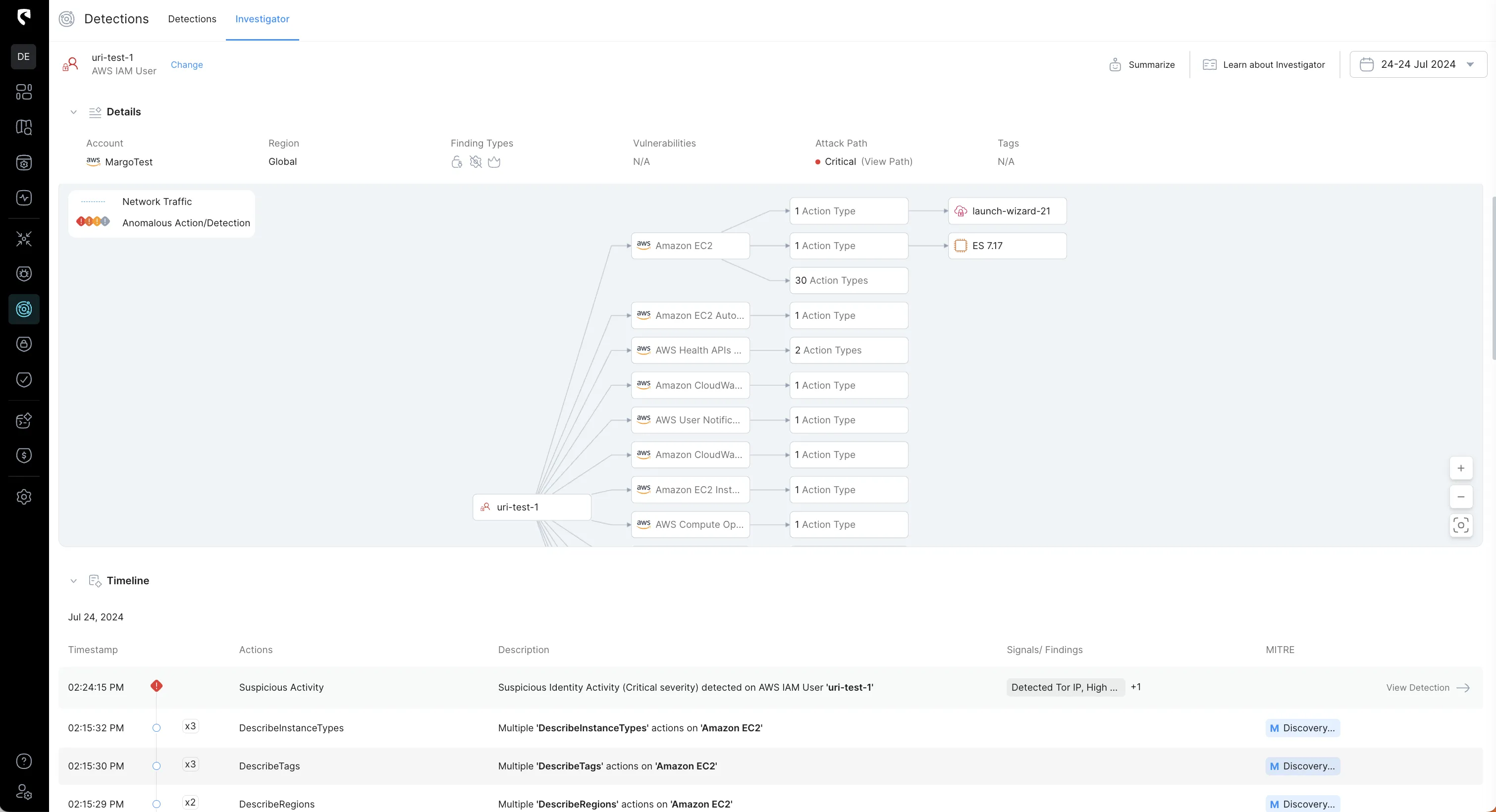
To streamline the investigation process, Stream automatically correlates all events related to an attack based on specific principles, such as user activity and privilege escalation during lateral movement. It then provides investigators with a clear, comprehensive view of the incident via a graph – the Investigator:
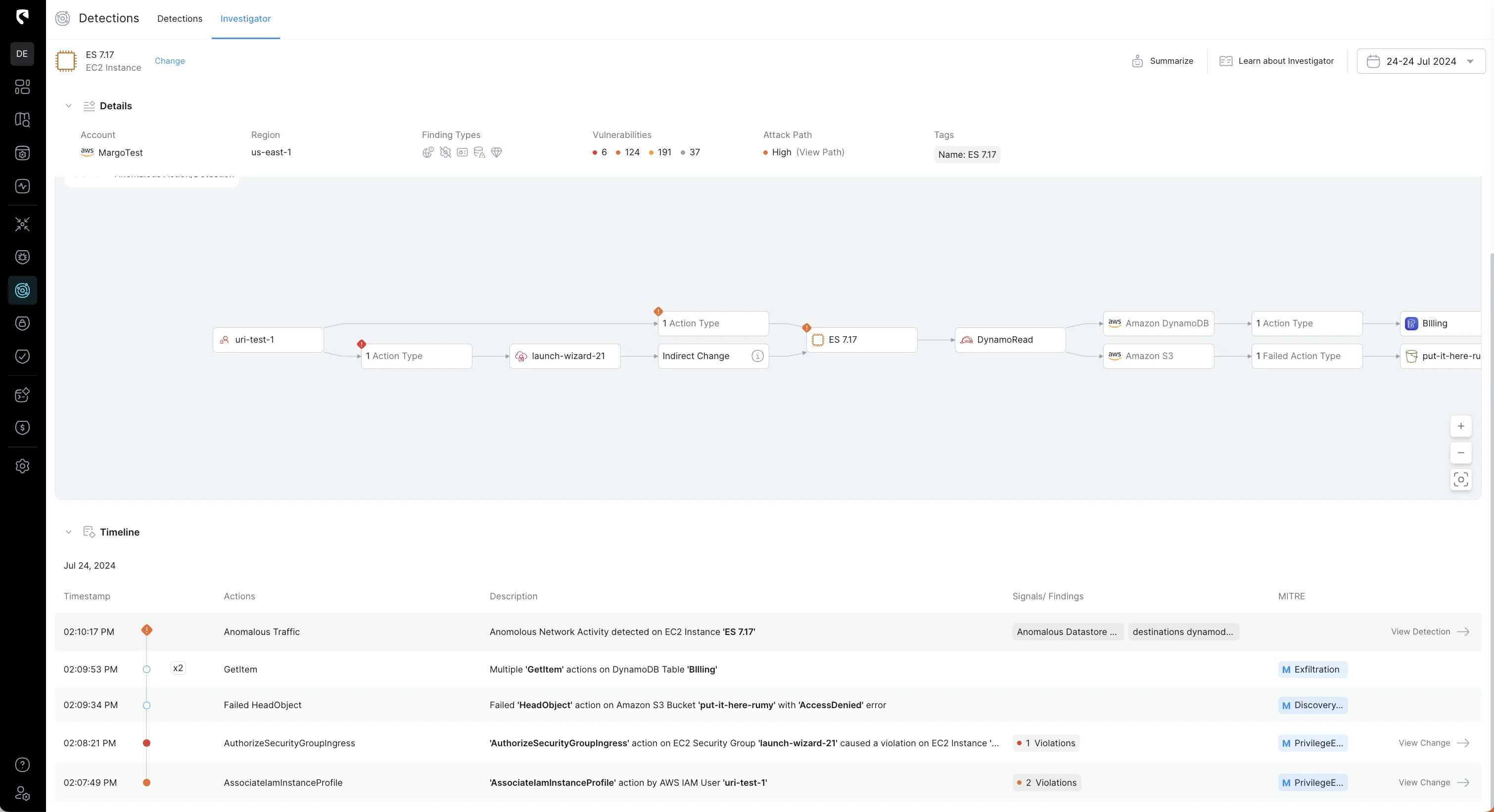
5. Reviewing the Timeline of Actions
Examination of the instance's activity timeline reveals that the attacker executed the AssociateIamInstanceProfile action, resulting in two high-severity configuration changes:
- Resource with over permissive DynamoDB GetItem permissions
- Resource has access to get data from Crown Jewel DynamoDB
6. Assessing Security Group Modifications
The attacker proceeded to perform the AuthorizeSecurityGroupIngress action on a Security Group, which effectively granted SSH access (port 22) to the compromised EC2 instance, increasing the risk of unauthorized access.
7. Failed Access Attempt on S3 Bucket
The attacker attempted the HeadObject action on an S3 bucket but encountered an 'AccessDenied' error, indicating restricted access to certain data.
8. Multiple GetItem Actions on DynamoDB
Despite the failed attempt on the S3 bucket, the attacker continued by performing multiple GetItem actions on a DynamoDB table, aiming to extract valuable information.
9. Correlation with Anomalous Network Activity
All these actions collectively resulted in the detected anomalous network activity from the EC2 instance, confirming the legitimacy of the initial alert.
10. Reviewing the Attacker’s Attack Path
Additionally, the platform shows the potential next move of the attacker based on the available attack path, based on the current adversary foothold.
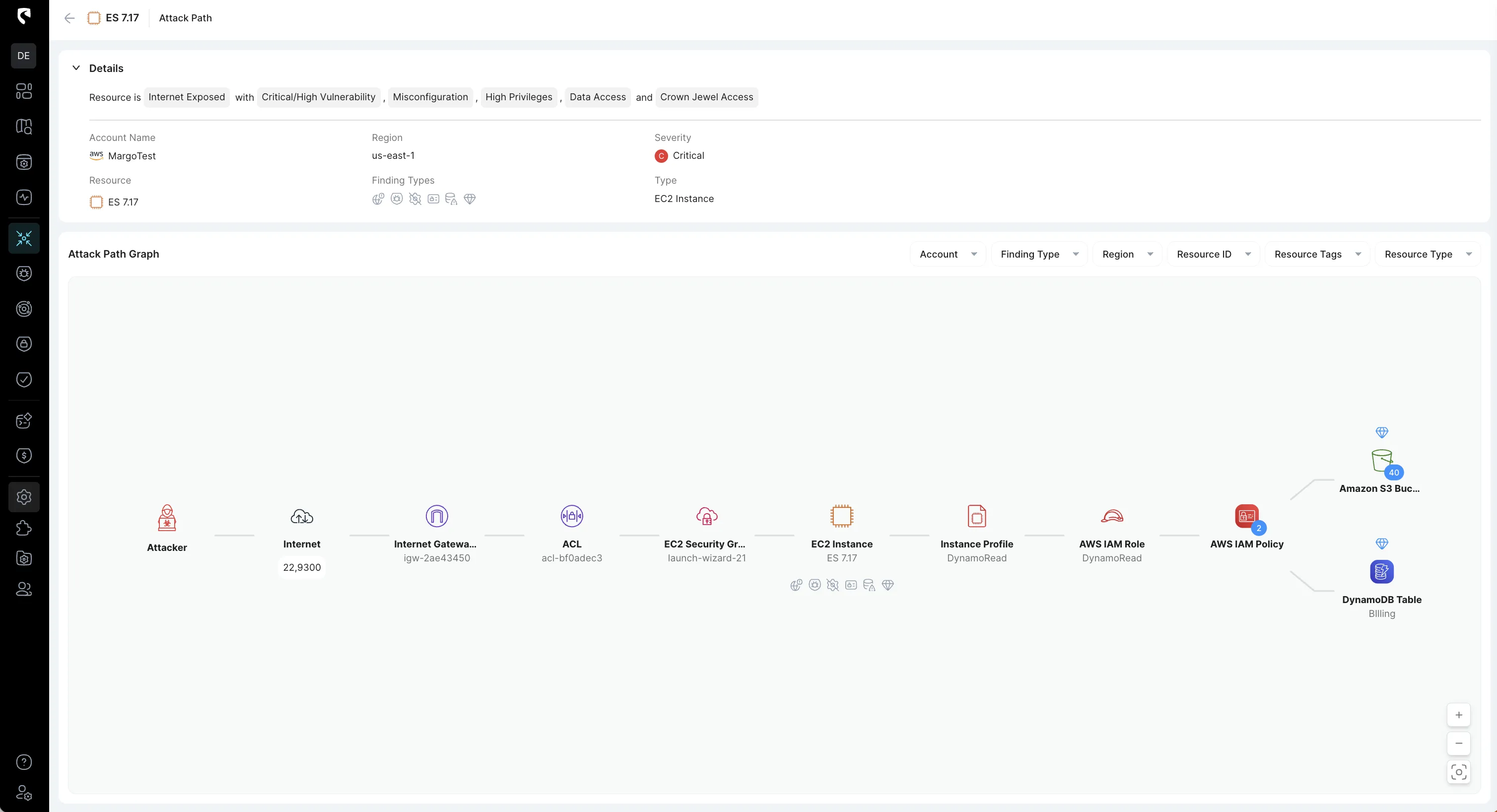
11. Triage and Assessing the Blast Radius
With a clear sequence of the attacker’s actions and their attack path, the security team can triage the incident effectively. They assess the blast radius to determine the potential impact and scope of the breach, identifying all affected systems and data.
12. Identifying the Attack Source
Instead of spending hours manually correlating contextless logs while the adversary advances their attack, Stream's investigation quickly identifies the attacker's origin as a Tor IP address, confirming the activity as malicious rather than a false positive. This insight solidifies the understanding of the threat and the necessary steps for mitigation.
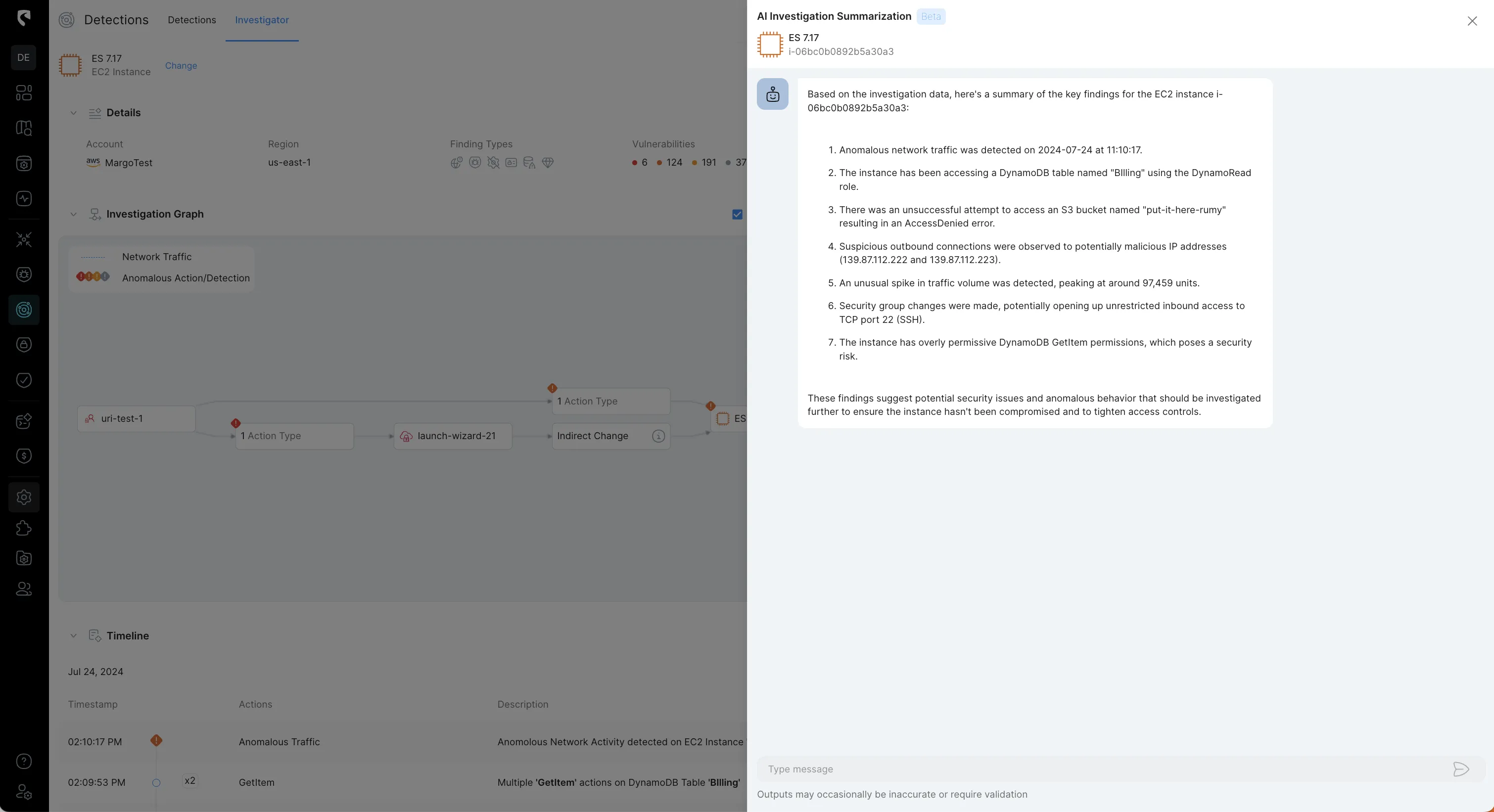
13. Utilizing Generative AI for Summarization and Reporting
To effectively communicate the status of an investigation to various stakeholders, Stream provides a business-level summary of the attack storyline, making it easy for everyone to understand and enabling quick, informed decision-making. Stream's generative AI feature further enhances this process by efficiently summarizing the entire investigation and generating actionable recommendations with just a click.
The challenges of threat detection in the cloud are significant, given the dynamic nature of cloud environments and the complex, interconnected systems involved. Investigating threats effectively requires tools that provide not just alerts but comprehensive context.
A Cloud Detection and Response (CDR) tool with capabilities like real-time analysis of security and compliance implications, detailed tracking of configuration changes, and clear visualization of attack paths can make a significant difference. The solution helps security teams to get the entire cloud context needed to quickly identify the root cause of an issue, understand the full scope of an attack (including the blast radius), and see the impact of every change within the cloud environment.
By integrating these insights, security teams can prioritize threats more effectively, streamline investigations, and resolve issues with a clear understanding of the interconnected risks. This context-driven approach allows organizations to respond faster and more accurately to threats, ultimately enhancing their overall cloud security posture.
Stream.Security delivers the only cloud detection and response solution that SecOps teams can trust. Born in the cloud, Stream’s Cloud Twin solution enables real-time cloud threat and exposure modeling to accelerate response in today’s highly dynamic cloud enterprise environments. By using the Stream Security platform, SecOps teams gain unparalleled visibility and can pinpoint exposures and threats by understanding the past, present, and future of their cloud infrastructure. The AI-assisted platform helps to determine attack paths and blast radius across all elements of the cloud infrastructure to eliminate gaps accelerate MTTR by streamlining investigations, reducing knowledge gaps while maximizing team productivity and limiting burnout.


