In Amazon Web Services (AWS), an idle resource is a computing resource that is provisioned but not actively utilized or performing any meaningful work or processing. This can include various types of resources, such as virtual machines, databases, storage volumes, load balancers, and other services that are provisioned but not actively used. Idle resources in AWS can consume unnecessary computing power and resources, leading to higher costs and reduced system efficiency. It is important to detect and address idle resources to optimize resource utilization, reduce costs, and improve overall system performance. AWS provides various tools and services to help users identify and manage idle resources, such as AWS CloudWatch, AWS Trusted Advisor and AWS Cost Explorer. By regularly monitoring and optimizing idle resources, organizations can ensure they are only paying for the resources they need and are making the most of their AWS investment.
It is important to detect idle resources in AWS for several reasons:
Overall, detecting and managing idle resources in AWS is important for optimizing costs, improving resource allocation, enhancing security, and ensuring compliance. It is an essential part of managing your cloud infrastructure and can help you make the most of your AWS investment.
There are several resources in AWS that can become idle, which may result in unnecessary costs.
Here's a list of thesetop resources:
AWS provides several tools and services to help find idle compute and database resources, such as:
By using these tools and services, you can detect idle resources in your AWS environment and take action to optimize your usage and reduce costs.
Using Lightlytics Architectural Standards, you can quickly identify potentially idle resources that can be easily optimized. You can use Lightlytics’s out-of-the-box Idle Resources rules, or you can create your own custom rules using tags and various idle resources attributes. By using these capabilities, you can review the total predicted monthly cost of each rule, and a breakdown of cost per violated resource within each rule.
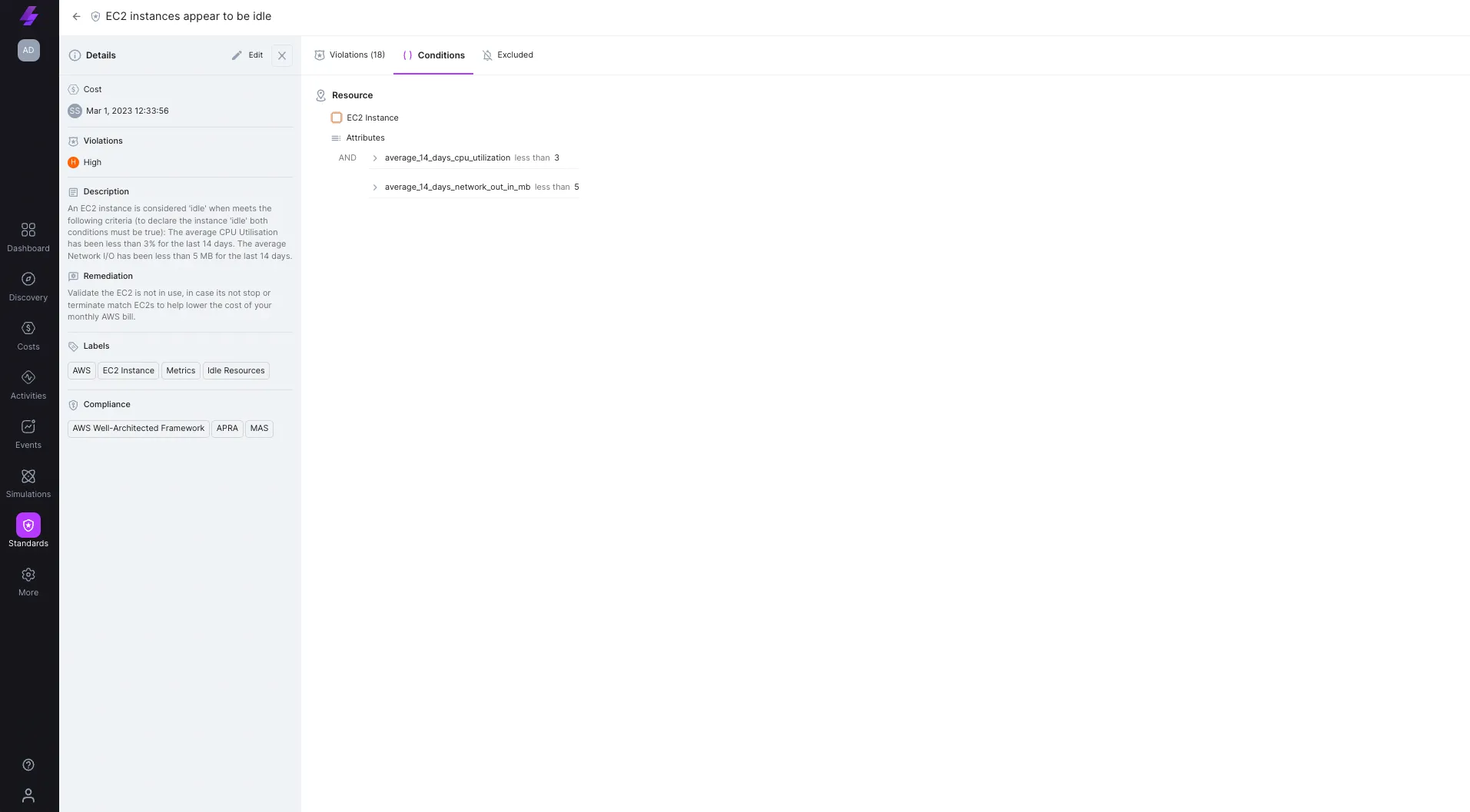
Example #1 architectural standard: EC2 instances appear to be idle
An EC2 instance is considered idle when both of the following terms are met:
1. The average CPU utilization has been less than 3% for the last 14 days
2. The average Network I/O has been less than 5 MB for the last 14 days
This rule can also help you work with the AWS Well-Architected Framework.
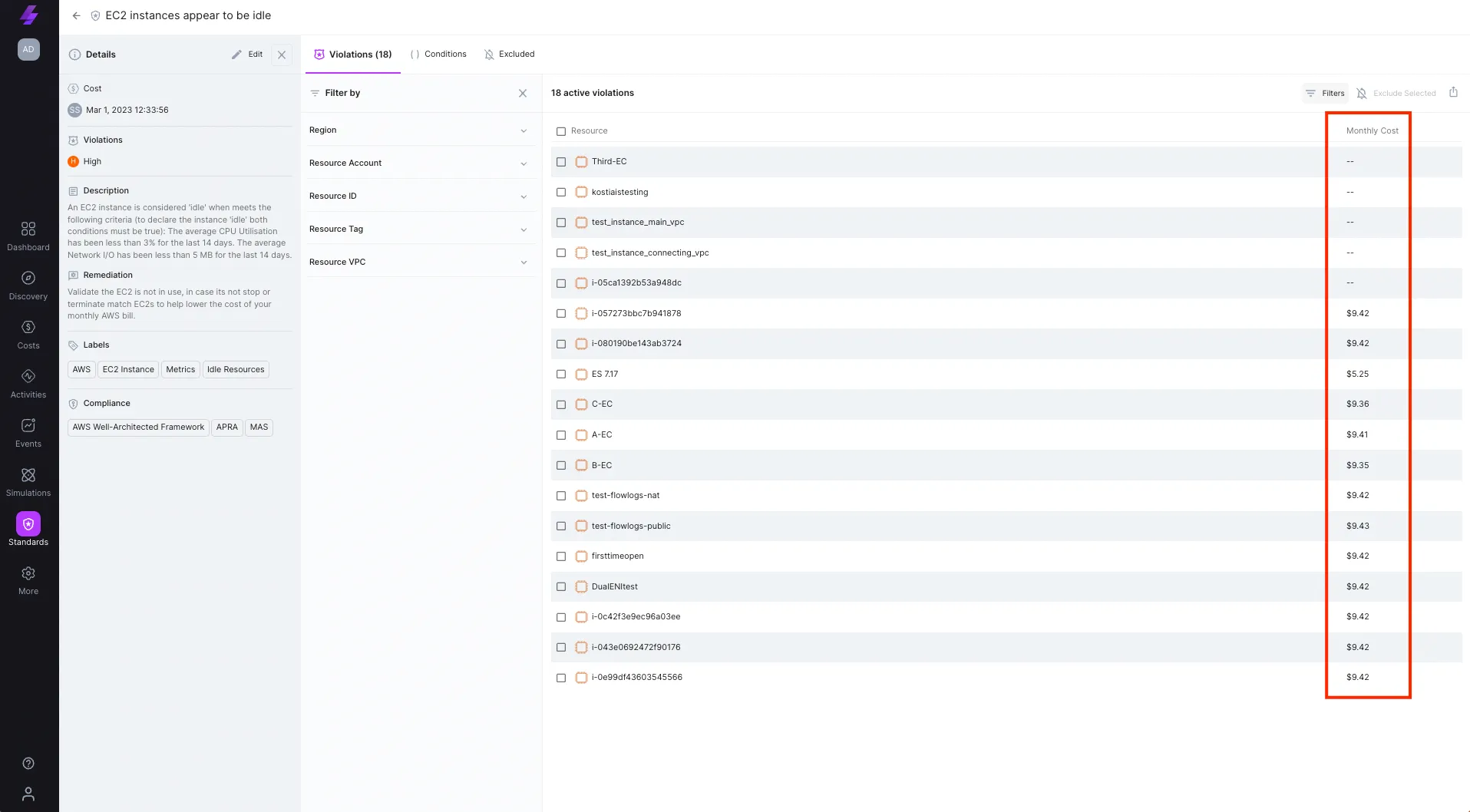
Review rule violations: When there are violations of this rule (or any rule in our architectural standards), this view shows each violated resource including the related monthly costs.
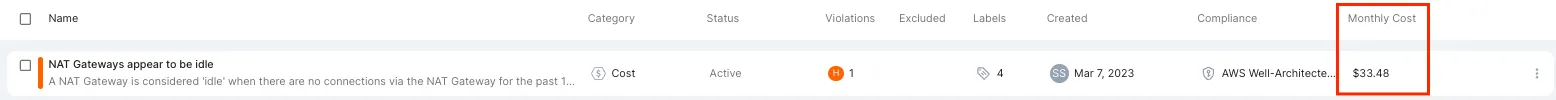
Example #2 architectural standard: NAT Gateways appear to be idle
A NAT Gateway is considered idle in case there were no connections via the NAT Gateway for the last 14 days.
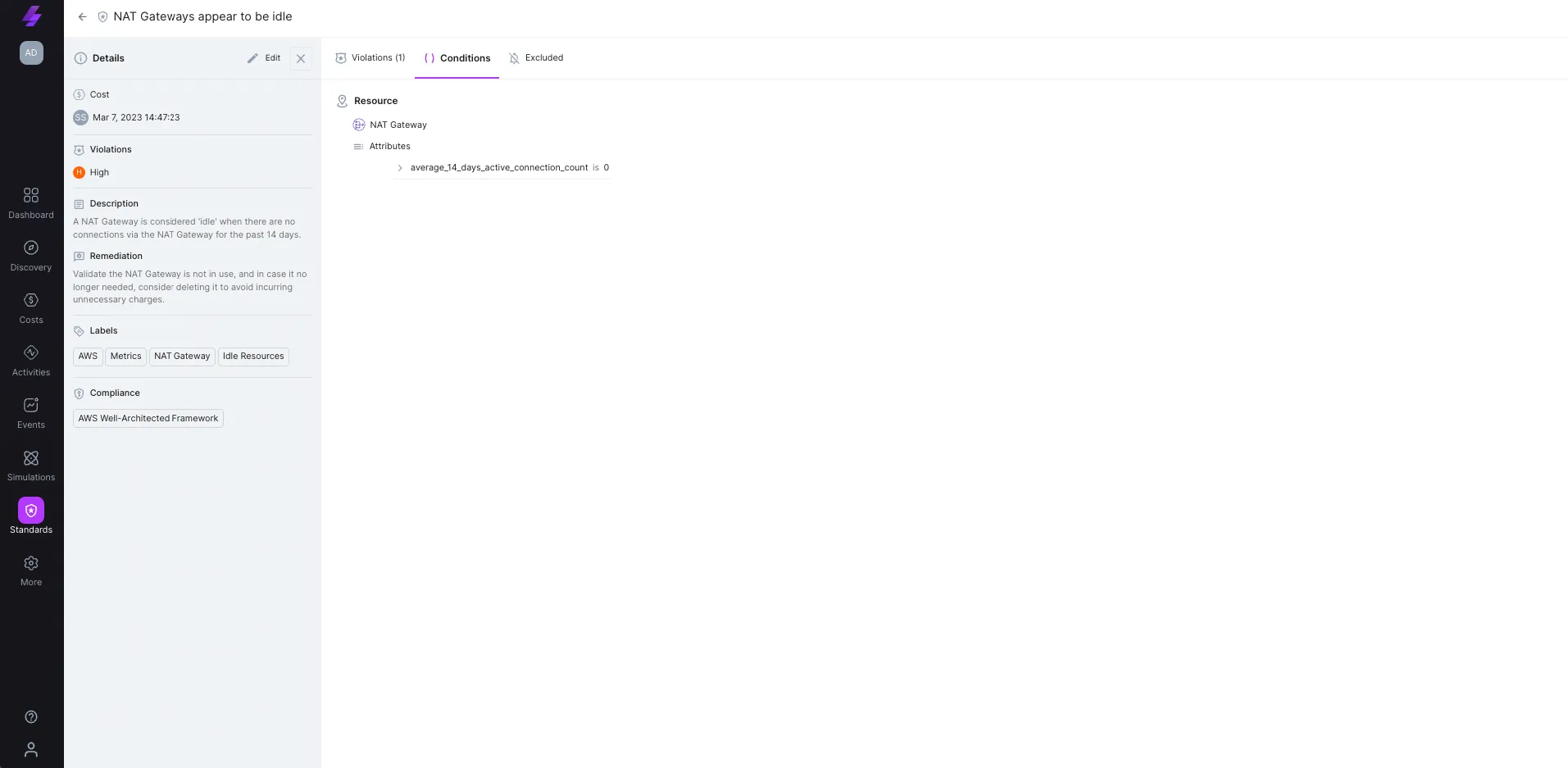
Review rule violations: When there are violations of this rule (or any rule in our architectural standards), this view shows each violated resource including the related monthly costs.
In conclusion, identifying and managing idle resources in AWS is a critical aspect of cost optimization and resource utilization in a cloud computing environment. By using the various tools and services provided by AWS, such as AWS CloudWatch, AWS Trusted Advisor, and AWS Cost Explorer, you can monitor and analyze resource usage patterns to identify idle resources and take appropriate actions, such as shutting down or resizing resources, to reduce costs and improve system efficiency.
Regularly monitoring and managing idle resources in AWS can help organizations avoid unnecessary expenses and maximize their return on investment in cloud computing. As organizations increasingly rely on cloud computing services, identifying and managing idle resources will continue to play a crucial role in maintaining optimal performance and cost efficiency in AWS.
Stream.Security delivers the only cloud detection and response solution that SecOps teams can trust. Born in the cloud, Stream’s Cloud Twin solution enables real-time cloud threat and exposure modeling to accelerate response in today’s highly dynamic cloud enterprise environments. By using the Stream Security platform, SecOps teams gain unparalleled visibility and can pinpoint exposures and threats by understanding the past, present, and future of their cloud infrastructure. The AI-assisted platform helps to determine attack paths and blast radius across all elements of the cloud infrastructure to eliminate gaps accelerate MTTR by streamlining investigations, reducing knowledge gaps while maximizing team productivity and limiting burnout.
