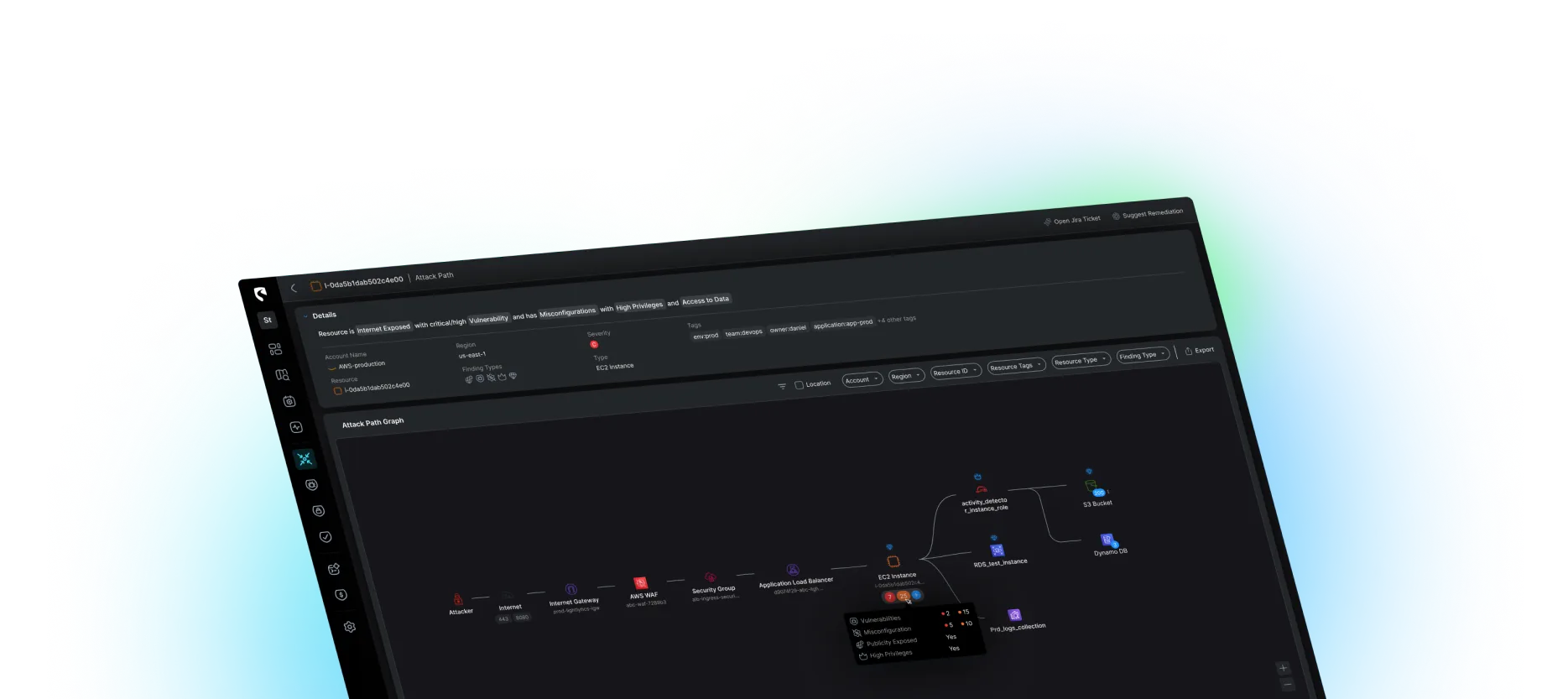
Stream.Security’s CloudTwin™ technology equips your SecOps team with real-time visibility into your entire cloud infrastructure. The CloudTwin™ builds a real-time, synchronous model of your cloud environment that changes as your infrastructure evolves, giving your team complete cloud visibility to prepare for a potential attack.
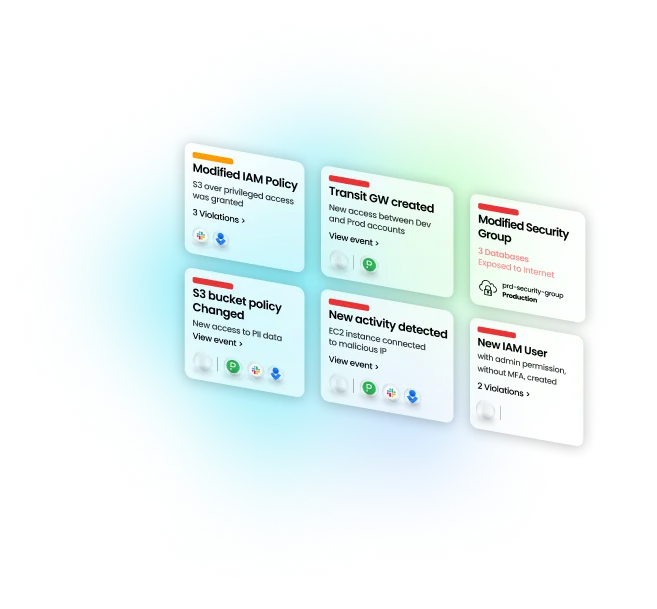
Confidently validate alerts before an attack escalates. With Stream Traps, strategically place deception assets that create high-fidelity signals to inform your team of a breach detection as part of the end-to-end detection & response process. As threat actors navigate the trap, your security team will have more time to mitigate, minimizing damage to your most sensitive data.
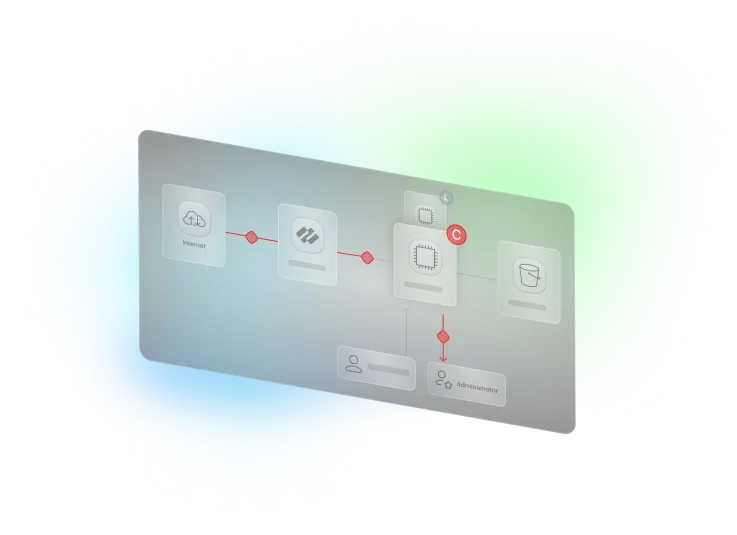
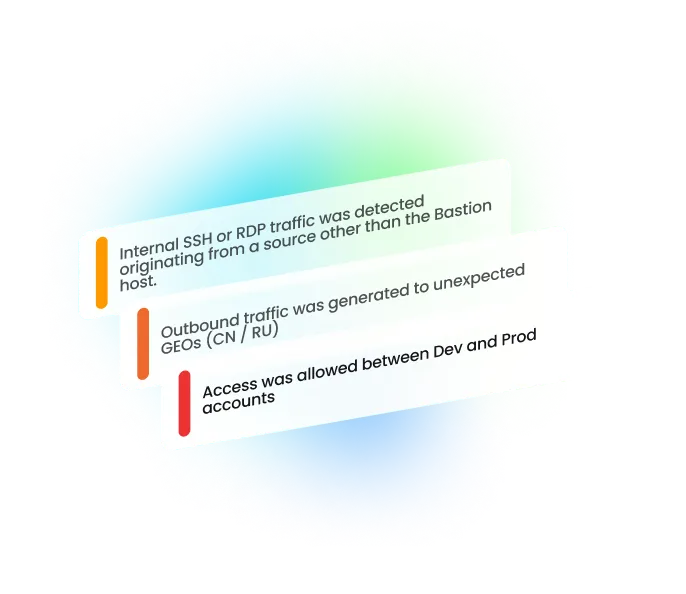
Enrich your existing detection capabilities with continuous monitoring across multi-cloud environments. CloudTwin™ detects malicious behavior across identity, data, network, K8s, and compute resources in real-time. Stream’s detection tools conduct advanced triaging using cloud context to measure blast radius and potential exploitability.
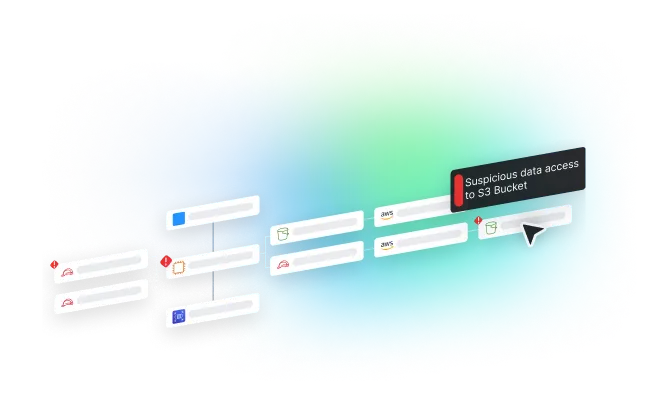
Investigate threats with a dynamic visual attack storyline that seamlessly connects network data, cloud identities, workloads, and audit logs to uncover the root cause of an attack. Correlate logs by principal, conduct impact analysis, and understand the true blast radius of a breach’s impact.
Respond to threats with surgical precision to minimize downtime.
Full cloud visibility allows your security team to target only affected systems for rapid response guided by an AI assistant that delivers actionable insights and response recommendations to boost efficiency.