

IAM plays a crucial role in securing access to resources in an AWS EKS cluster. It’s important to follow best practices when configuring IAM roles and policies to ensure that access is granted only to those who need it.
To troubleshoot IAM issues in EKS, it is important to:
These tips and best practices can help you identify and resolve IAM issues quickly and efficiently.
When working with Amazon EKS, it’s important to have a strong understanding of IAM (Identity and Access Management) to effectively troubleshoot any issues that may arise. Here are some tips and best practices to help you troubleshoot IAM issues in EKS, along with some detailed code examples:
In EKS, the Kubernetes Service Account is used to authenticate and authorize requests to the Kubernetes API server. When troubleshooting IAM issues, it’s important to check the Service Account to ensure that it has the correct IAM permissions.
Here’s an example of how you might check the Service Account for a worker node in EKS:
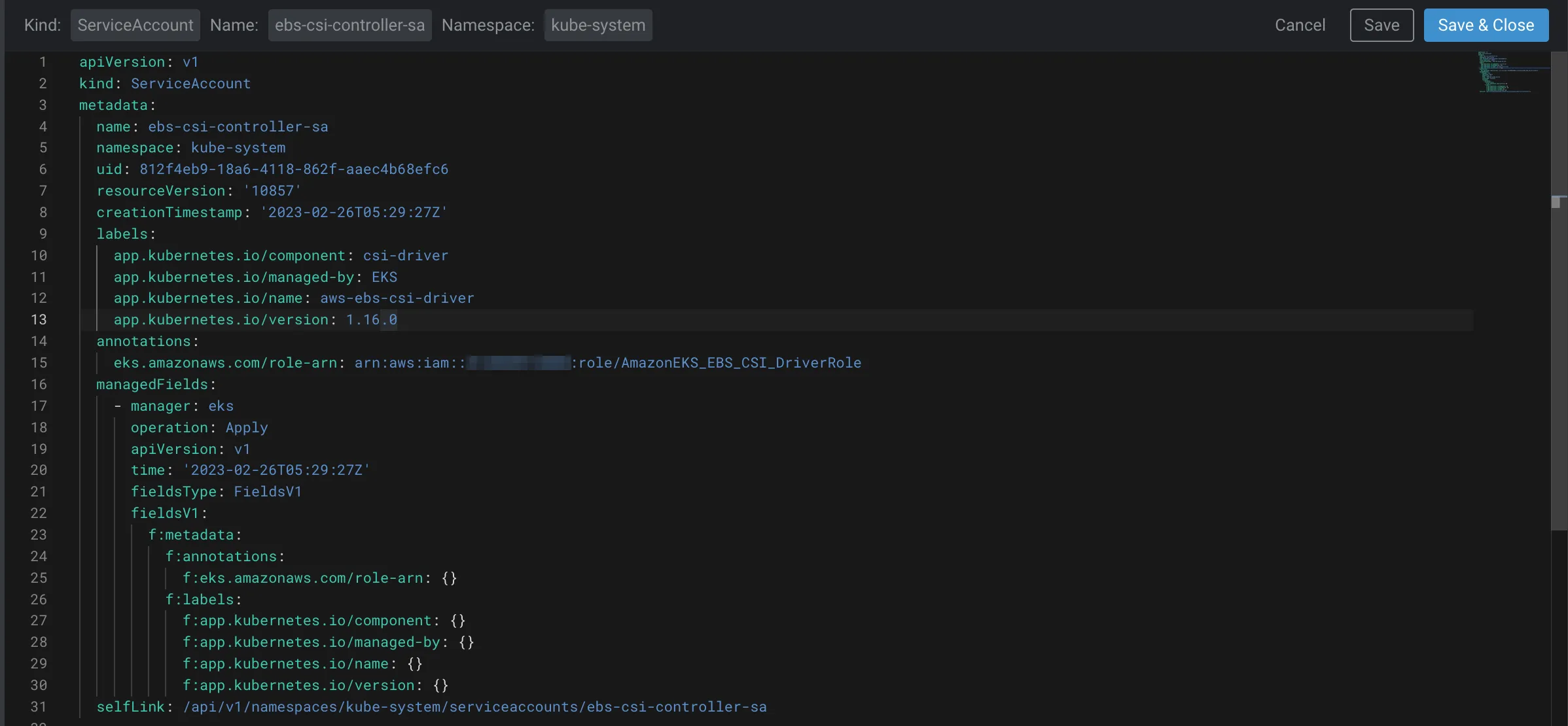
kubectl describe sa <service-account-name>
This command will return information about the Service Account, including the IAM role that it’s associated with. If the Service Account doesn’t have the correct IAM permissions, you can update it using the following command:
eksctl create iamidentitymapping --cluster <cluster-name> --namespace <namespace> --serviceaccount <service-account-name> --arn <iam-role-arn>
This command will create a mapping between the Service Account and the IAM role, allowing the Service Account to access the necessary resources.
If you’re experiencing IAM issues in EKS, it’s important to check the IAM policies and permissions that are associated with the relevant roles. Here’s an example of how you might check the IAM policies associated with a specific role:
aws iam list-attached-role-policies --role-name <role-name>
This command will return a list of policies that are attached to the specified IAM role. If you find that the IAM policies or permissions are incorrect, you can update them using the following command:
aws iam put-role-policy --role-name <role-name> --policy-name <policy-name> --policy-document <policy-document>
This command will update the specified IAM policy with the new policy document.
In EKS, the Kubernetes ConfigMap is used to store IAM roles and permissions that are applied to the Kubernetes control plane and worker nodes. When troubleshooting IAM issues, it’s important to verify that the correct IAM role and permissions are being applied in the ConfigMap. Here’s an example of how you might check the ConfigMap for a worker node in EKS:
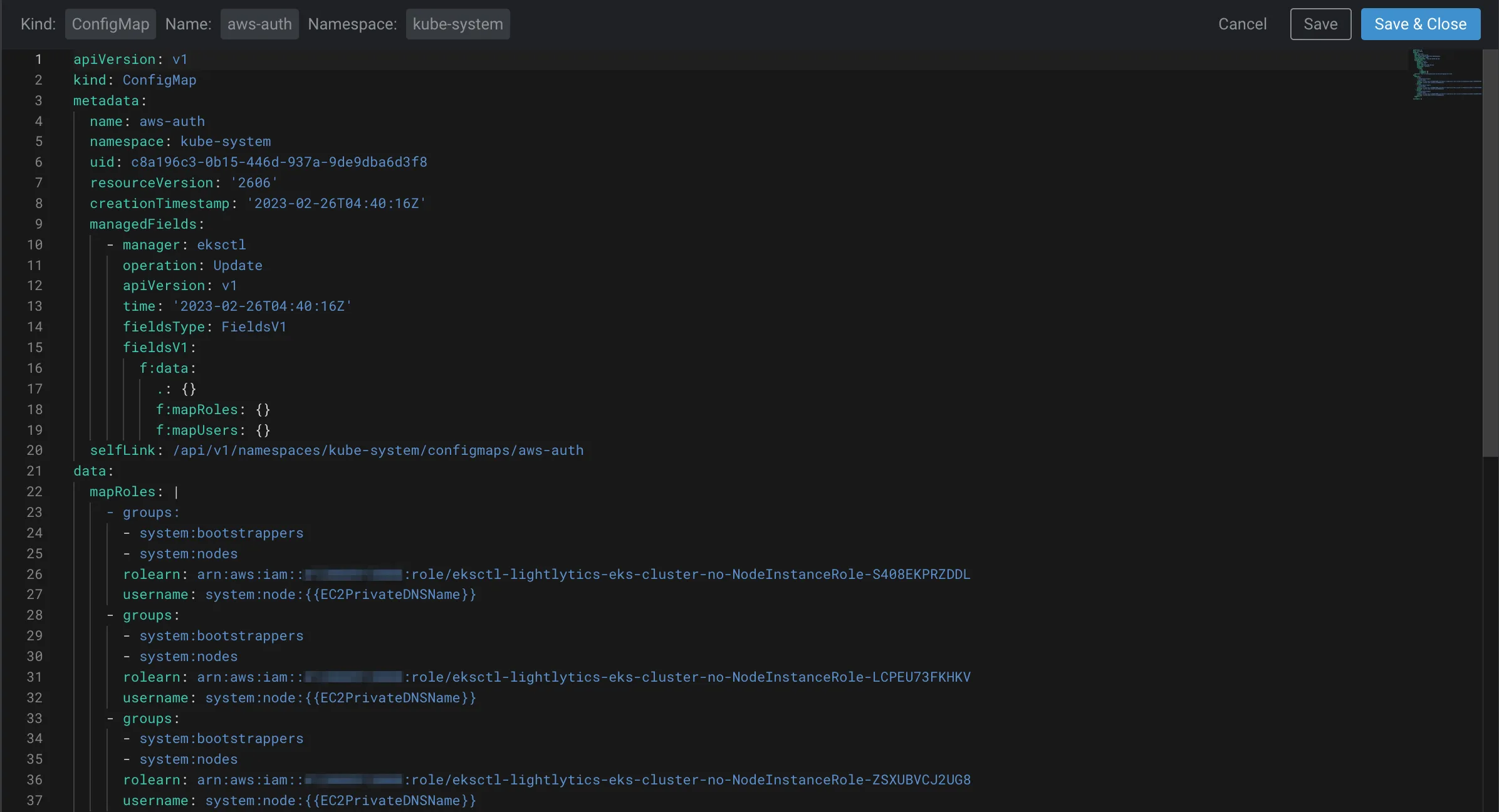
kubectl describe configmap aws-auth -n kube-system
This command will return information about the ConfigMap, including the IAM roles and permissions that are associated with the Kubernetes control plane and worker nodes. If you find that the IAM roles or permissions are incorrect, you can update the ConfigMap using the following command:
kubectl edit configmap aws-auth -n kube-system
This command will open the ConfigMap YAML file in your default editor, allowing you to make changes to the IAM roles and permissions.
AWS CloudTrail is a service that can be used to monitor and log AWS API activity, including IAM activity. When troubleshooting IAM issues in EKS, it’s a good idea to use CloudTrail to monitor IAM activity and identify any potential issues.
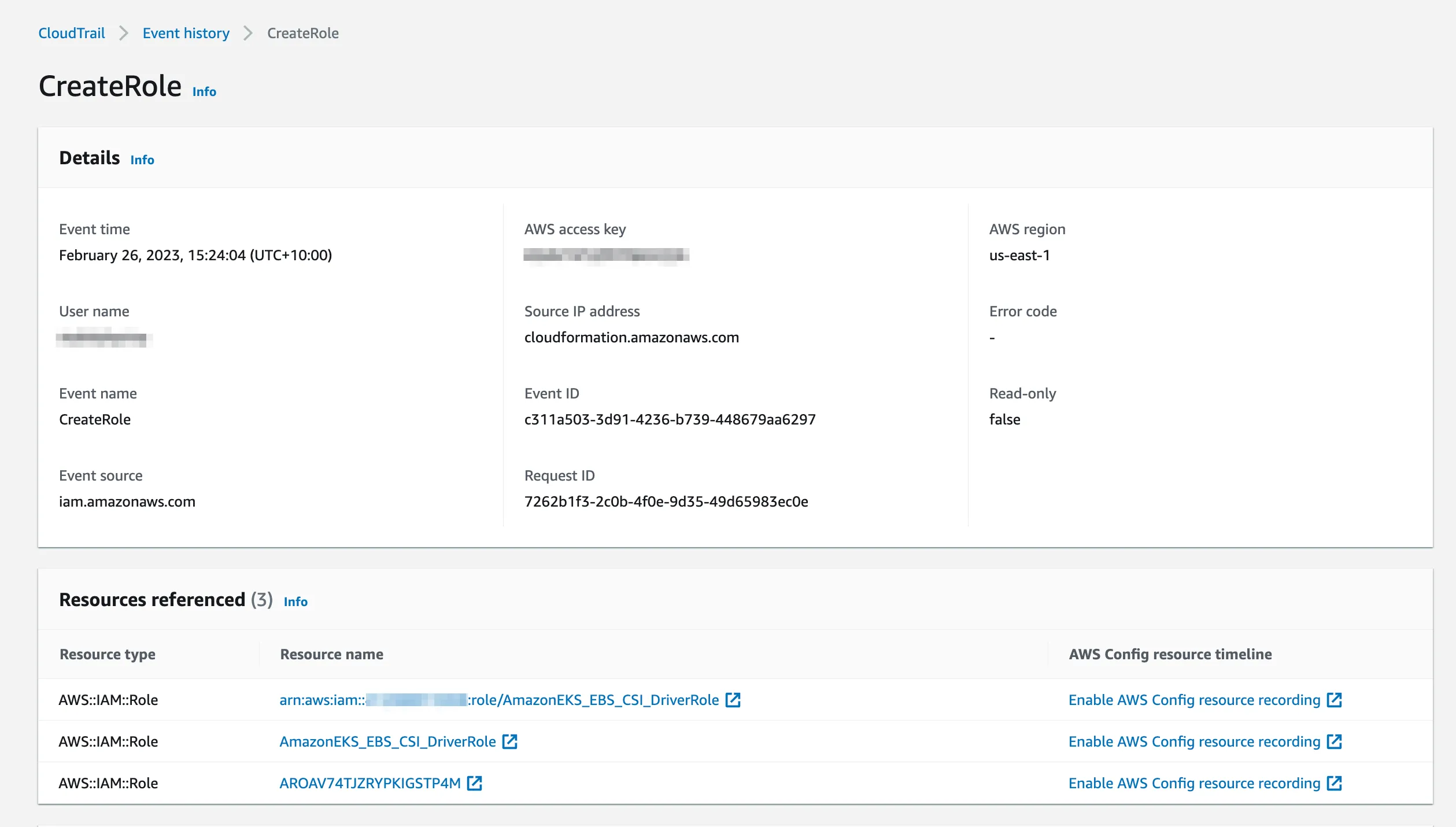
Here’s an example of how you might use CloudTrail to monitor IAM activity:
aws cloudtrail create-trail –name <trail-name> --s3-bucket-name <bucket-name> --is-multi-region-trail
This command will create a new CloudTrail trail that logs all IAM activity to the specified S3 bucket. You can then use the AWS Management Console to view the CloudTrail logs and identify any potential issues with IAM activity in EKS.
The AWS Identity and Access Management (IAM) Access Analyzer is a service that can be used to identify and prevent unintended access to resources. When troubleshooting IAM issues in EKS, it’s a good idea to use the Access Analyzer to identify any potential issues with IAM permissions or policies. Here’s an example of how you might use the IAM Access Analyzer to identify potential issues:

aws accessanalyzer create-analyzer --analyzer-name <analyzer-name> -- type ACCOUNT
This command will create a new IAM Access Analyzer that can be used to identify any potential issues with IAM permissions or policies in your AWS account. You can then use the AWS Management Console or the AWS CLI to review the findings of the IAM Access Analyzer and take corrective action if necessary.
Amazon GuardDuty is a threat detection service that continuously monitors malicious activity and unauthorized behaviour in your AWS account. It can be used to detect and troubleshoot IAM issues in EKS.
Here’s an example of how you might use GuardDuty to troubleshoot IAM issues in EKS:
1. Enable GuardDuty in your AWS account:
aws guardduty create-detector --enable
2. Configure GuardDuty to monitor for IAM-related events:
aws guardduty create-filter --detector-id <detector-id> --name <filter-name> --action ARCHIVE --rank 1 --finding-criteria '{"criterion": {"service": {"eq": ["iam.amazonaws.com"]}}}'
This command will create a filter that instructs GuardDuty to monitor for IAM-related events.
3. Review GuardDuty findings to identify potential IAM issues:
aws guardduty list-findings --detector-id --region
This command will return a list of GuardDuty findings, including any potential IAM issues that have been detected. You can then use the AWS Management Console or the AWS CLI to investigate these findings and take corrective action if necessary. By using GuardDuty to monitor for IAM-related events, you can quickly detect and troubleshoot any potential IAM issues in EKS, helping to keep your applications secure and running smoothly.
By following these best practices, you can effectively troubleshoot IAM issues in EKS and ensure that your applications are running smoothly and securely.
In conclusion, IAM plays a crucial role in securing access to resources in an EKS cluster. It’s important to follow best practices when configuring IAM roles and policies to ensure that access is granted only to those who need it.
To troubleshoot IAM issues in EKS, it is important to check IAM roles and permissions, use RBAC rules, review Kubernetes API server logs, use AWS CLI commands, review AWS documentation, check security groups, use kubectl commands, check AWS CloudTrail, and use IAM Access Analyzer. These tips and best practices can help you identify and resolve IAM issues quickly and efficiently.
In addition, regularly reviewing and updating your IAM roles and policies, RBAC rules, and security groups can prevent potential security risks and unauthorized access attempts. By following these best practices, you can maintain a secure and reliable EKS environment and ensure that your Kubernetes resources are only accessed by authorized users and services.
We're obviously biased, but using Lightlytics can help you gain unmatched visibility into your EKS and AWS, save you tons of time and heartache too! Check out our interactive demos to see how we can help today!
Stream.Security delivers the only cloud detection and response solution that SecOps teams can trust. Born in the cloud, Stream’s Cloud Twin solution enables real-time cloud threat and exposure modeling to accelerate response in today’s highly dynamic cloud enterprise environments. By using the Stream Security platform, SecOps teams gain unparalleled visibility and can pinpoint exposures and threats by understanding the past, present, and future of their cloud infrastructure. The AI-assisted platform helps to determine attack paths and blast radius across all elements of the cloud infrastructure to eliminate gaps accelerate MTTR by streamlining investigations, reducing knowledge gaps while maximizing team productivity and limiting burnout.

